- Proxy Server Deceptions – Misleading Claims and Silent Installations
- The Trap of Cracked Software and Games
- The Proxy’s Dual Purpose
- The Monetization Challenge
- Insights on the AdLoad Saga
- The Evolution of Malware Strategy
- MacOS – The New Battleground
- A Deeper Dive into the MacOS Threat Landscape
- Conclusion
In the vast digital expanse, cybercriminals are showcasing their technical prowess by skillfully harnessing the vulnerabilities present in malware-infected computers, spanning both the Windows and macOS platforms. By implanting a proxy server application within these compromised systems, they ingeniously convert them into exit nodes. These nodes then play a pivotal role in rerouting and redirecting proxy requests, often serving malicious ends.
Remarkably, a certain company that has delved into this dubious service claims to operate an extensive network of over 400,000 proxy exit nodes. However, the real concern surfaces when one considers the clandestine manner in which an undetermined portion of these nodes are taken over by malicious software, all happening covertly without the slightest hint to the oblivious end-users.
Proxy Server Deceptions – Misleading Claims and Silent Installations
On the surface, the proxy service website exudes confidence, reassuring its user base that they have been duly informed and have granted explicit consent for their devices to function as exit nodes in this intricate web. This creates an aura of trust and transparency for the end-users.
However, in a sharp contrast to these claims, the renowned cybersecurity behemoth, AT&T Alien Labs, has unveiled some deeply unsettling insights. Their rigorous investigations and research point towards a sinister practice wherein cyber adversaries are craftily and silently embedding the proxy software onto vulnerable systems. This means that a significant number of users could be unwittingly caught in this net, unaware of the covert operations their machines are entangled in.
The Trap of Cracked Software and Games
There’s an alarming trend of various malware strains introducing the proxy to individuals lured by the promise of cracked software and games. Crafted in the Go programming language, this proxy software is designed to target both macOS and Windows. Especially on Windows, it’s incredibly discreet, effortlessly dodging detection due to a legitimate digital signature.
The Proxy’s Dual Purpose
Far from being just a rudimentary tool for redirecting traffic, the intricacies of this proxy software go well beyond the surface. It operates on multiple levels, not only managing incoming and outgoing requests but also continuously communicating with its overseeing master server. As it seamlessly integrates itself into the compromised host, it cunningly extracts a wealth of system-specific data.
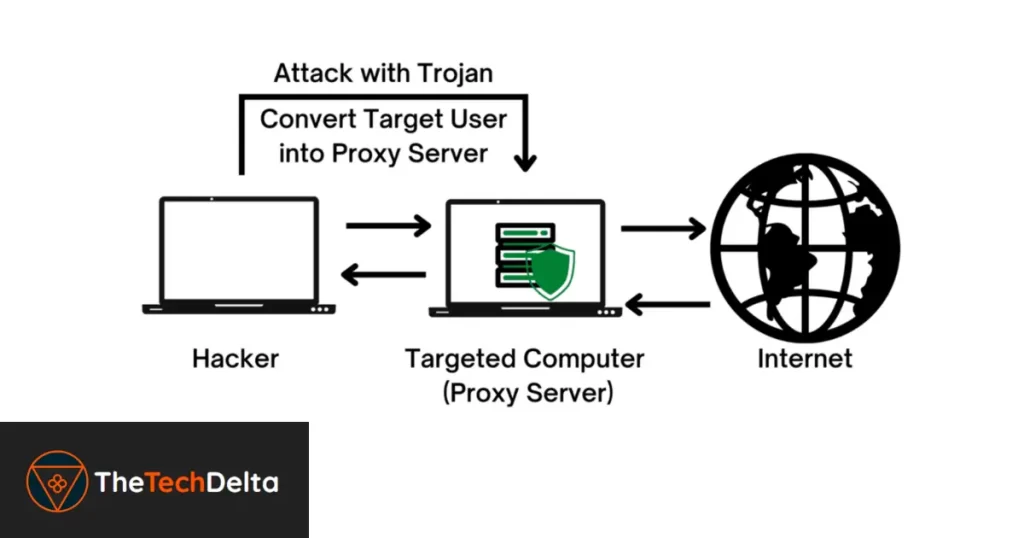
This treasure trove of data encompasses details as intricate as the system’s CPU and memory performance metrics, extending to seemingly benign aspects like the battery health of the device. But the proxy’s covert operations don’t stop there. The act of its installation often serves as a portentous sign, foreshadowing the imminent incursion of additional malicious elements, be it malware or adware. This subsequent invasion amplifies the vulnerability of the already compromised system, pushing its defenses to the brink.
The Monetization Challenge
The cybersecurity community holds Ofer Caspi in high esteem, recognizing him as an authority on security research. When he speaks, the industry listens. Recently, Caspi voiced his apprehensions in clear, unequivocal terms. He pointed out a burgeoning trend where attackers are leveraging an affiliate-based revenue model to reap financial benefits from malware-laden proxy servers.
By adopting this strategy, Caspi emphasized, cybercriminals not only enhance their monetization efforts but also facilitate a faster spread of these threats. “By embedding a systematic channel like the affiliate model,” Caspi elaborated, “we’re witnessing an expedited distribution mechanism for these malicious entities, potentially exacerbating the overall cyber threat landscape.”
Insights on the AdLoad Saga
Revisiting prior revelations by AT&T highlights that macOS devices corrupted by AdLoad adware join an expansive residential proxy botnet. AdLoad, renowned for masquerading as reputable applications, tricks users into visiting perilous websites. This elaborate ruse subsequently provides cybercrooks with profitable opportunities. As AT&T stated, “This sweeping AdLoad infiltration impacting potentially thousands globally underscores the enticing potential macOS users represent for these malicious entities.”
The Evolution of Malware Strategy
The strategic pivot of malware towards proxy apps underlines the shrewdness of cyber adversaries. Lured by lucrative returns and driven by affiliate initiatives, these proxies serve as vehicles for ill-gotten gains, often hidden behind captivating offers or tarnished software.
MacOS – The New Battleground
MacOS systems have recently emerged as a goldmine for cybercriminals. A staggering 1,000% spike in the dark web’s listings of macOS-targeted information-stealing tools has been observed since 2019. Reports from Accenture further confirm the heightened threat activity surrounding macOS in 2022 and 2023, citing its rising adoption in the corporate sphere and the vast monetary potential it offers to attackers.
A Deeper Dive into the MacOS Threat Landscape
Hailing from Romania, the cybersecurity titan Bitdefender delved deep into the threats beleaguering the Mac user community. Their meticulous research bore revealing insights. Mac aficionados, they found, are primarily besieged by a trinity of cyber threats. Leading the pack are the Trojans, accounting for a staggering 51.8%. Following closely are Potentially Unwanted Applications (PUAs) at 25.3%, and then, the persistent menace of Adware, making up 22.6%. In this landscape of threats, one particular malevolent software stands out – EvilQuest.
According to Bitdefender’s analysis, this nefarious entity alone shoulders a massive 52.7% of the entire threat spectrum targeting Mac systems. The company’s findings also came with a stern warning: Trojans, ever-evolving and insidious, have a penchant for exploiting vulnerabilities left unpatched. They emphasized the peril that lurks when users, either due to oversight or procrastination, neglect to promptly implement vital security patches rolled out by Apple.
Conclusion
The intricate web of proxy servers, malware, and the ever-evolving threat landscape underscores the need for heightened vigilance and proactive cybersecurity measures. As technological advancements soar, so do the threats that accompany them. Users, whether on Windows or macOS, must remain informed, cautious, and always prioritize their digital security ensuring vigilance is set to paramount importance.
As the cybersecurity landscape continues to evolve, it is essential to stay informed about emerging threats and developments. I would highly suggest you to visit our Cyber Safety section to enhance your defenses and stay ahead of evolving cyber threats.
If you found these cybersecurity updates valuable, don’t miss out on more exclusive content. Follow us on Twitter and Instagram to stay informed about emerging threats and developments. Join our community and gain access to the latest cybersecurity trends to bolster your defense against evolving risks.



