The Akira ransomware group has become a significant threat in the cybersecurity domain, collecting a staggering $42 million from over 250 victims by January 1, 2024.
Initially focusing on businesses and critical infrastructure across North America, Europe, and Australia since March 2023, the group’s recent expansion into targeting Linux servers underscores a worrisome escalation in their strategies and capabilities.
This shift represents a pivotal moment in the group’s evolution, indicating a broader and potentially more impactful reach in their nefarious activities.
As they diversify their targets and tactics, the Akira group poses an increasingly complex challenge to cybersecurity professionals and organizations worldwide. Lets understand the complexities in more details below.
Also Read : GenAI in SaaS Poses New Challenges for Security Teams
Evolution of Akira Ransomware
Originally, Akira ransomware focused solely on Windows operating systems. However, in April 2023, they redirected their attention to VMware ESXi virtual machines, introducing a new Linux variant.
This transition underscores the group’s adaptability and readiness to capitalize on vulnerabilities across diverse platforms, aiming to enhance their influence and profits.
Such flexibility demonstrates the sophistication of their operations and highlights the need for comprehensive cybersecurity measures to counter their evolving tactics effectively.
As they continue to expand their reach and capabilities, organizations must remain vigilant and proactive in safeguarding their systems against this ever-evolving threat landscape.
Tactics and Techniques
Akira ransomware gains initial access to target networks through various means, including exploiting known vulnerabilities in Cisco appliances and utilizing techniques like Remote Desktop Protocol (RDP) and spear-phishing.
Once inside a network, the group establishes persistence and evades detection by employing sophisticated methods such as creating new domain accounts and terminating antivirus processes using vulnerable drivers.
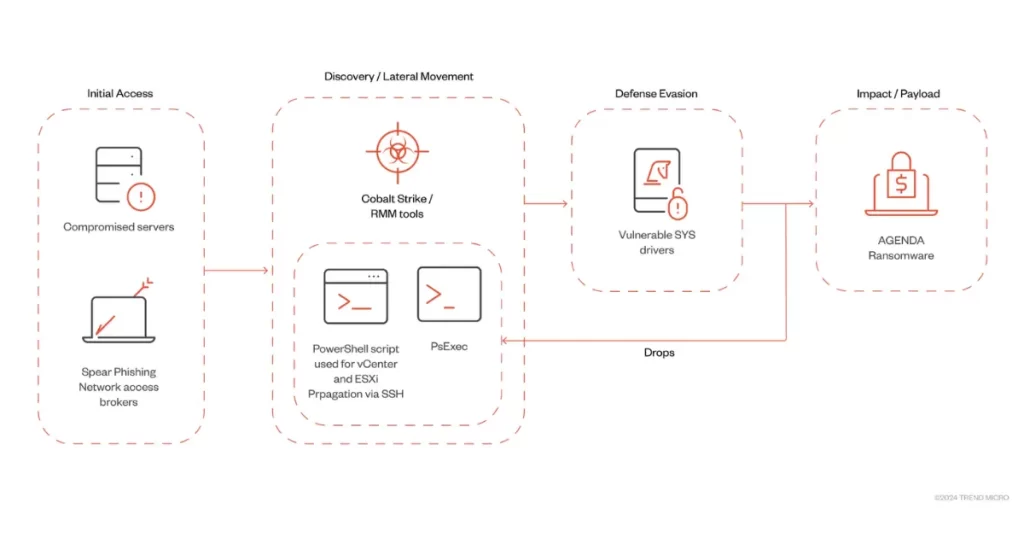
To escalate privileges and move laterally within the network, Akira actors leverage credential scraping tools like Mimikatz and utilize Windows RDP.
Data exfiltration is achieved through a range of tools including FileZilla, WinRAR, WinSCP, and RClone, highlighting the comprehensive nature of their operations.
Encryption and Affiliations
Akira ransomware employs a hybrid encryption algorithm that combines Chacha20 and RSA, blending two different methods to secure their malicious activities.
This dual-layered encryption approach adds complexity to decryption attempts, significantly complicating the process for victims trying to regain access to their encrypted files.
When analysts delve into the blockchain and source code data related to Akira ransomware, they uncover intriguing connections hinting at possible affiliations with the now-defunct Conti ransomware gang.
These findings suggest a deeper, more intricate network of cybercriminal activity lurking beneath the surface.
Such associations could indicate collaborative efforts or shared resources among different ransomware groups, emphasizing the interconnected nature of cyber threats in today’s digital landscape.
Impact on the Cyber Landscape
The appearance of Akira ransomware targeting Linux servers mirrors a pattern seen in various other well-known ransomware groups.
This trend indicates a troubling pivot towards exploiting weaknesses within enterprise infrastructures. Meanwhile, the recent dismantling of the LockBit group by law enforcement has triggered notable consequences.
In response, the group has resorted to employing deceptive maneuvers in a bid to recoup lost momentum.
LockBitSupp, the alleged leader of LockBit, seems to be trying to make it look like they have more victims. They’re also focusing on countries where law enforcement tried to stop them, according to Trend Micro’s recent investigation.
This demonstrates the resilience and adaptability of cybercriminal organizations in the face of legal interventions.
Response and Future Challenges
As cybersecurity experts remain vigilant, observing and dissecting the actions of ransomware groups like Akira, they also confront the evolving threat landscape.
One concerning development is the rise of “junk-gun ransomware,” which presents a new set of challenges. These rudimentary yet effective tools, available at low cost and accessible to individual threat actors, enable them to unleash impactful attacks with considerable profit potential.
This emergence of amateur cyber weaponry amplifies the complexity of defending against such threats, requiring innovative strategies and heightened preparedness from defenders.
Conclusion
The rise of Akira ransomware and its expansion to target Linux servers underscore the evolving nature of cyber threats and the need for robust defense mechanisms.
By understanding the tactics and techniques employed by threat actors, organizations can better prepare themselves to detect, mitigate, and recover from ransomware attacks.
Collaboration between law enforcement agencies, cybersecurity researchers, and industry stakeholders is essential to combatting this growing menace and safeguarding digital infrastructure and assets.
If you found these security learnings valuable, don’t miss out on more exclusive content. Follow us on Twitter and Instagram to stay informed about emerging threats and developments.
Check out the Cyber Safety Section and Subscribe our Newsletter, Join our community and gain access to the latest cybersecurity trends to bolster your defense against evolving threats & associated risks 🙂