Cloudzy, a relatively obscure Iranian entity, is under increasing scrutiny as it stands accused of facilitating various threat actors, including sophisticated cybercriminal collectives and even state-sponsored hacking teams. Despite its business origins being officially rooted in the United States, the firm is not beyond the investigative radar of cybercrime experts.
One such authority, Halcyon, a prominent cybersecurity firm headquartered in Texas, presents a compelling argument suggesting that Cloudzy’s primary operations are not based in the U.S. as initially believed. Halcyon asserts that the company likely carries out its activities from Tehran, Iran. Such a geographical operational pivot could potentially place the company at odds with U.S. sanctions, thus intensifying the controversial narrative surrounding it.
Moreover, the cybersecurity firm posits that the individual suspected of spearheading this operation goes by the name of Hassan Nozari. As per Halcyon’s claims, Nozari is purportedly running the show from behind the scenes, drawing more attention to the organization’s activities.
These alleged connections, if proven, could stir up a significant cybercrime controversy, implicating an international web of operations and further highlighting the urgent need for comprehensive cybersecurity measures globally. Cloudzy’s case, therefore, opens up a Pandora’s box, revealing the complex and often hidden structures supporting the cybercrime underworld.
Cloudzy’s Role as a Command and Control Provider
Cloudzy’s alleged activities pivot on acting as a command-and-control provider (C2P). C2Ps deliver virtual private servers through Remote Desktop Protocol (RDP) and other anonymized facilities, which are key tools exploited by ransomware accomplices and other cyber offenders for executing their unlawful pursuits. Halcyon points out a loophole in liability law, which means C2Ps don’t have to verify that their services are not utilized for illegal actions.
Ransomware as a Service Business Model and C2P Providers
The Ransomware-as-a-Service (RaaS) business model has grown increasingly complex, consisting of core developers, affiliates who execute the attacks for a share of the spoils, and initial access brokers who utilize vulnerabilities or hijacked credentials to gain access, which they subsequently sell to affiliates.
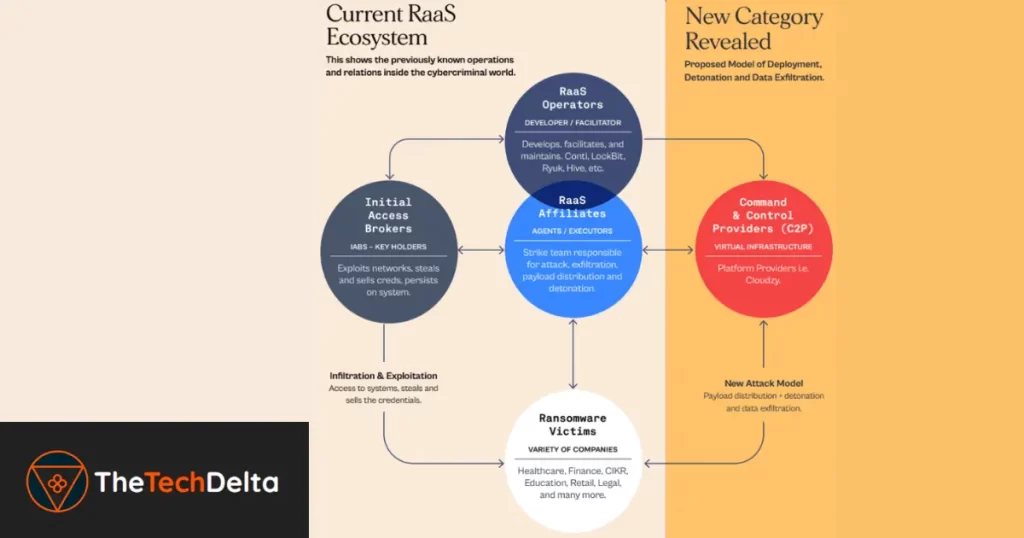
Emerging in this framework are C2P providers, another group of actors who, knowingly or unwittingly, supply the infrastructure to facilitate these attacks.
Key Players Alleged to Utilize Cloudzy
Cloudzy is believed to be facilitating an array of state-backed entities and cybercrime organizations from numerous countries. These include China’s APT10, India’s Sidewinder, Iran’s APT33 and APT34, North Korea’s Kimsuky, Konni, and Lazarus Group, Pakistan’s Transparent Tribe, Russia’s APT29 and Turla, and Vietnam’s OceanLotus, along with cybercrime entities such as Evil Corp and FIN12. Two ransomware associates, namely Ghost Clown and Space Kook, who employ the BlackBasta and Royal ransomware strains respectively, and the contentious Israeli spyware vendor Candiru, are also implicated.
Possible Misuse and Abuse of Cloudzy
The speculation is that ill-intentioned actors are exploiting the ease with which VPS services can be bought from Cloudzy. The only requirements are a functioning email address and anonymous cryptocurrency payment, thus presenting an avenue ripe for exploitation. This has led to suspicions that threat actors could be weaponizing lesser-known firms like Cloudzy to propel significant hacks.
Cloudzy’s Stance on Misuse and Abuse
Cloudzy’s own website bears a support document that states, “If your VPS server is suspended because of misuse or abusive usage such as prohibited uses: Phishing, Spamming, Child abuse, Attacking other people, etc., there is a $250-$1000 fine or NO WAY for unsuspension; this depends on the complaint type.”
The Larger Attack Apparatus and Role of C2P Entities
While C2P entities, including Cloudzy, may seem to be bona fide businesses, it’s possible they might not even be aware of the misuse of their platforms for illicit campaigns. However, they inevitably form an essential pillar of the broader attack machinery employed by some of the most sophisticated threat actors.
Conclusion
As cybersecurity evolves to keep pace with the new methods adopted by cyber criminals, it’s crucial to scrutinize entities like Cloudzy that could potentially be leveraged for illegal activities. Greater oversight of C2P providers may be needed to prevent them from unknowingly becoming tools in the hands of cybercriminals, reinforcing the infrastructure for cyber threats. As the case of Cloudzy highlights, even seemingly legitimate businesses can be drawn into the dark underbelly of the cybercrime world, necessitating greater vigilance and regulatory enforcement.
As the cybersecurity landscape continues to evolve, it is essential to stay informed about emerging threats and developments. I would highly suggest you to visit our Cyber Safety section to enhance your defenses and stay ahead of evolving cyber threats.
If you found these cybersecurity updates valuable, don’t miss out on more exclusive content. Follow us on Twitter and Instagram to stay informed about emerging threats and developments. Join our community and gain access to the latest cybersecurity trends to bolster your defense against evolving risks.