North Korean hackers are suspected to have created a new Apple macOS malware named RustBucket, used to download and execute multiple payloads. The malware is attributed to BlueNoroff, a subgroup of the Lazarus cluster known for sophisticated heists aimed at SWIFT systems and cryptocurrency exchanges.
BlueNoroff’s attacks are said to have shifted significantly in recent months to using job-themed lures to trick email recipients into entering their credentials on fake landing pages. This adaptation of the toolset to accommodate cross-platform malware is an indication that threat actors are adapting their methods, which may be alarming for security teams.
New Tactics of North Korean hackers
Lazarus Group, an umbrella term for a mixture of state-sponsored and criminal hacking groups within the Reconnaissance General Bureau (RGB), North Korea’s primary foreign intelligence apparatus, is known for using native malware for all major desktop operating systems: Windows, macOS, and Linux. Recently, the group was found to be behind cascading supply chain attacks using trojanized installers of a legitimate app to breach enterprise communications software maker 3CX and poison its Windows and macOS apps.
Lazarus Group is currently showing a growing interest in exploiting trust relationships in the software supply chain as entry points to corporate networks. This strategy is being pursued at a time of busy activity by the group, with numerous attacks aimed at organizations worldwide to collect strategic intelligence and perform cryptocurrency theft.
BlueNoroff’s RustBucket
The RustBucket malware is designed to look like an “Internal PDF Viewer” application to activate the infection. It is an AppleScript file that retrieves a second-stage payload from a remote server, which also bears the same name as its predecessor. Both the malicious apps are signed with an ad-hoc signature.
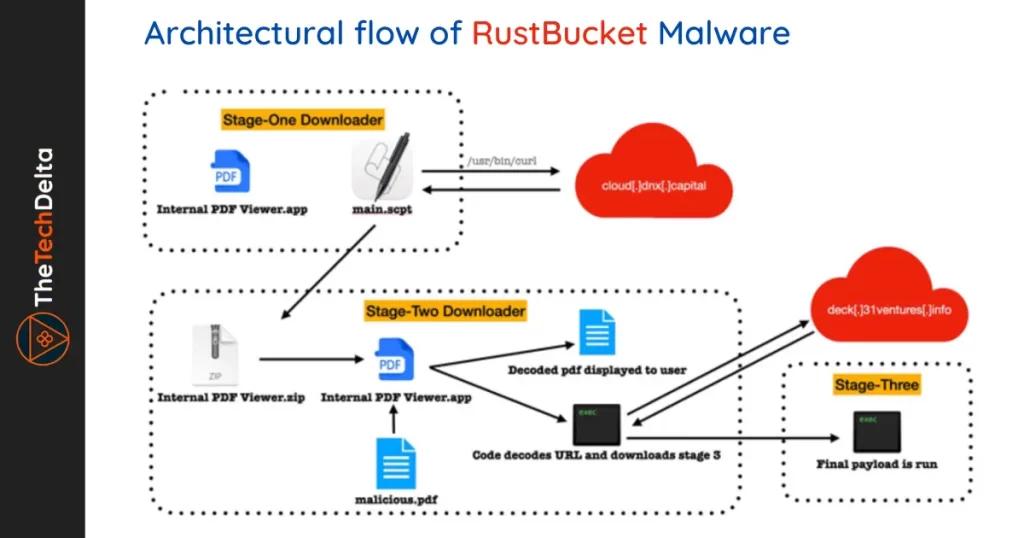
The second-stage payload is a basic application written in Objective-C that claims to offer the ability to view PDF files. However, it only initiates the next phase of the attack chain when a booby-trapped PDF file is opened through the app. When such a nine-page PDF document purporting to offer an “investment strategy” is launched, it reaches out to the command-and-control (C2) server to download and execute a third-stage trojan. This Mach-O executable is written in Rust and comes with capabilities to run system reconnaissance commands.
Jamf Threat Labs researchers, Ferdous Saljooki, and Jaron Bradley explained that “This PDF viewer technique used by the attacker is a clever one,” adding that “At this point, in order to perform analysis, not only do we need the stage-two malware, but we also require the correct PDF file that operates as a key to execute the malicious code within the application.”
Shift in Attack Strategy
BlueNoroff’s attack repertoire has shifted significantly in recent months to using job-themed lures to trick email recipients into entering their credentials on fake landing pages. This strategy indicates that the threat actor is adapting its methods to cross-platform malware using programming languages such as Go and Rust.
With RustBucket, Apple users are at risk of having their devices infected, which underscores the need for a multi-layered security strategy. It is essential to keep the software up-to-date, have security software installed, and continuously monitor the network for suspicious activity.
Conclusion
BlueNoroff’s RustBucket malware is a new threat to macOS users attributed to Lazarus subgroup, known for cyber heists. They use job-themed lures to trick users and adapt to cross-platform malware using languages like Go and Rust. A multi-layered security approach is necessary, including email filtering, anti-malware software, and security awareness training. Additional measures like network segmentation and intrusion detection systems should be considered. Users should avoid suspicious links and update their software. It’s crucial to stay informed and follow best practices for cybersecurity to reduce the risk of falling victim to evolving threats like RustBucket.



