A recently discovered malware strain named AVrecon has raised concerns as it specifically targets small office/home office (SOHO) routers. Over a span of two years, this malware has successfully infiltrated more than 70,000 devices, resulting in the creation of a botnet comprising 40,000 nodes spread across 20 countries.
Lumen Black Lotus Labs, a cybersecurity firm, has identified AVrecon as the third strain of its kind, following ZuoRAT and HiatusRAT, to focus on SOHO routers in the past year. In this article, we delve into the details of AVrecon, its global impact, and the potential motives behind its creation.
The Scope of AVrecon’s Infiltration
AVrecon has infiltrated a vast number of devices, making its impact truly significant. The majority of infected devices are concentrated in highly developed countries like the United Kingdom and the United States, reflecting the malware’s ability to penetrate even well-protected networks. However, AVrecon’s reach extends far beyond these regions. Infections have been detected in diverse countries such as Argentina, Nigeria, Brazil, Italy, Bangladesh, Vietnam, India, Russia, and South Africa, among others.
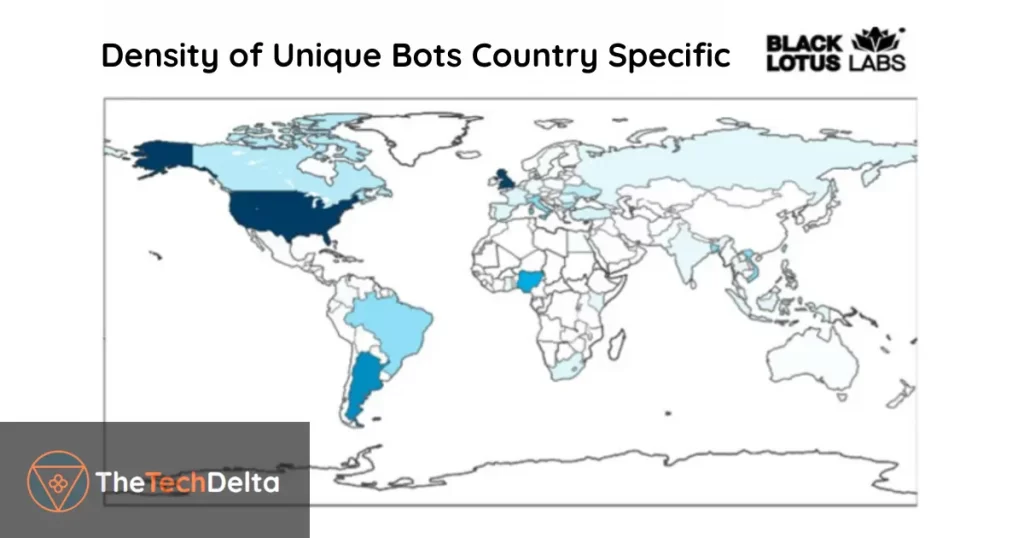
This global spread emphasizes the magnitude of the threat and underscores the pressing need for immediate countermeasures to protect networks and data from this pervasive malware. By taking proactive steps to strengthen security measures, organizations and individuals can effectively mitigate the risks posed by AVrecon and prevent further proliferation of this dangerous botnet.
The Attack Chain and Modus Operandi
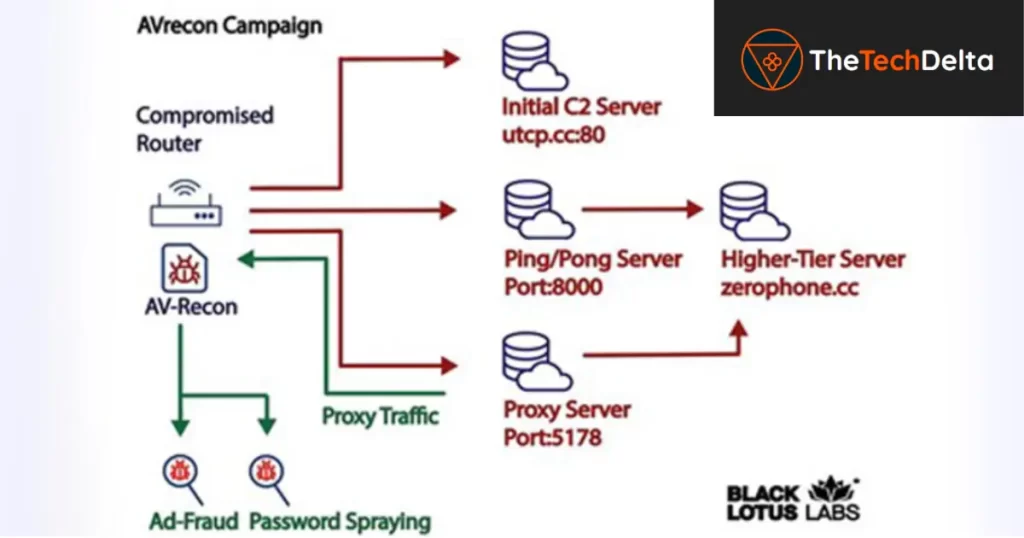
Lumen has provided insights into the attack chain employed by AVrecon. The initial stage involves infecting a target device, followed by enumerating the victim’s SOHO router and transmitting that information back to an embedded command-and-control (C2) server. To ensure effectiveness, AVrecon checks for the presence of other malware instances by searching for existing processes on port 48102 and terminates any such processes.
Subsequently, the compromised system establishes contact with a secondary C2 server, awaiting further instructions. Lumen has identified 15 unique servers involved in this operation, active since at least October 2021.
Technical Details and Infrastructure
AVrecon is written in the widely-used C programming language, enabling its easy portability across different architectures. Furthermore, the success of such attacks can be attributed to the exploitation of vulnerable infrastructure that lacks support for robust security solutions. Notorious botnets like Emotet and QakBot have also demonstrated the effectiveness of tiered C2 infrastructure, emphasizing the significance of this approach in the context of AVrecon.
Motives and Activities of AVrecon
The evidence collected thus far indicates that AVrecon primarily engages in two activities: engaging with Facebook and Google ads and interacting with Microsoft Outlook. This suggests a two-pronged effort involving advertising fraud and data exfiltration. The malware appears to focus on stealing bandwidth without impacting end-users, thereby creating a residential proxy service that facilitates the laundering of malicious activities while avoiding attention from Tor-hidden services or commercially available VPN services.
Conclusion
AVrecon represents a significant cybersecurity threat that has successfully infiltrated a vast number of SOHO routers worldwide. With its sophisticated attack chain and tiered C2 infrastructure, this malware strain has proven to be difficult to detect. The motives behind AVrecon’s creation encompass advertising fraud and data exfiltration, posing potential risks to both individuals and organizations. To mitigate the impact of AVrecon, it is crucial to employ robust security measures, update router firmware regularly, and stay vigilant against potential threats. By adopting proactive cybersecurity practices, we can ensure the protection of our digital ecosystems from evolving malware threats like AVrecon.
As the cybersecurity landscape continues to evolve, it is essential to stay informed about emerging threats and developments. I would highly suggest you to visit our CyberSecurity section to enhance your defenses and stay ahead of evolving cyber threats.
If you found these cybersecurity updates valuable, don’t miss out on more exclusive content. Follow us on Twitter and Instagram to stay informed about emerging threats and developments. Join our community and gain access to the latest cybersecurity trends to bolster your defense against evolving risks.



