The notorious threat actor known as ChamelGang has recently unveiled a new and undisclosed implant designed to infiltrate Linux systems, signaling a significant expansion of their capabilities. Named ChamelDoH by the esteemed security research group Stairwell.
This advanced malware leverages DNS-over-HTTPS (DoH) tunneling, representing a novel approach to covert communication.
The Menace of ChamelGang
Originally exposed by Russian cybersecurity firm Positive Technologies in September 2021, ChamelGang has gained infamy for its relentless attacks on critical infrastructure within fuel, energy, and aviation sectors.
Targeting organizations in Russia, the United States, India, Nepal, Taiwan, and Japan, the threat actor has demonstrated a sophisticated modus operandi, exploiting vulnerabilities in Microsoft Exchange servers and Red Hat JBoss Enterprise Application to gain initial access.
Notably, the group employed a passive backdoor named DoorMe, which operates as a native IIS module processing HTTP requests and responses, but solely targeting requests with specific cookie parameters.
The Discovery of ChamelDoH by Stairwell
Stairwell’s research has uncovered a Linux backdoor with capabilities that extend beyond information gathering. The ChamelDoH backdoor, identified by their diligent researchers, serves as a powerful tool for remote access, enabling functions like file upload, download, deletion, and shell command execution.
The Power of DNS-over-HTTPS or DoH
ChamelDoH distinguishes itself through its utilization of DNS-over-HTTPS (DoH) as a means of communication. DoH enables DNS resolution via the HTTPS protocol, employing DNS TXT requests directed to a rogue nameserver. This innovative approach poses challenges for security measures, as DoH providers like Cloudflare and Google, commonly used for legitimate traffic, cannot be easily blocked on an enterprise-wide level.
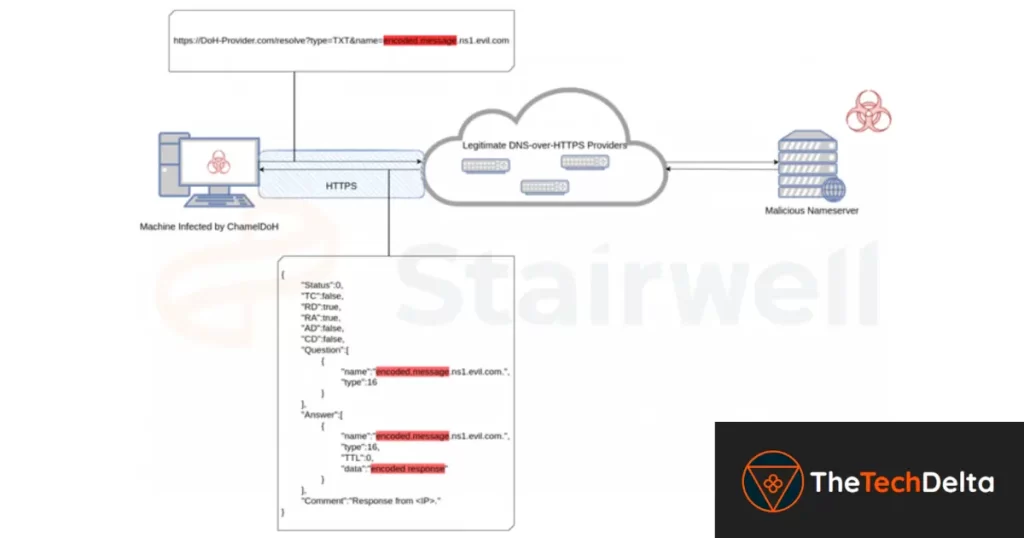
Additionally, the adoption of DoH for command-and-control (C2) purposes provides the threat actor with an extra layer of protection against interception attempts, as the HTTPS protocol ensures the requests are resistant to adversary-in-the-middle (AitM) attacks. Consequently, security solutions face difficulties in detecting and preventing malicious DoH requests, establishing an encrypted channel between compromised hosts and the C2 server. This tactic shares similarities with C2 via domain fronting, making it arduous to detect and impede communications.
ChamelDoH’s Alarming Presence of Samples
Stairwell’s researchers have encountered ten ChamelDoH samples on VirusTotal, with one of them being uploaded on December 14, 2022. The presence of these samples highlights the threat actor’s dedication to developing a robust toolset for Linux intrusions, amplifying concerns over the group’s capabilities and intentions.
Conclusion
The emergence of ChamelDoH, the Linux backdoor employed by the notorious threat actor ChamelGang, marks a disconcerting evolution in their offensive tactics.
By leveraging DNS-over-HTTPS tunneling, ChamelGang gains a significant advantage in conducting covert command and control operations. This sophisticated technique allows them to exploit legitimate DoH providers and encryption protocols, making it difficult for traditional security measures to detect and mitigate the risks posed by this advanced malware.
The implications of ChamelDoH underscore the urgent need for enhanced security measures. It is imperative for organizations to stay vigilant, update their defenses, and implement comprehensive monitoring and detection mechanisms to identify and respond to the presence of such advanced malware.
Proactive measures, including network segmentation, vulnerability patching, and user awareness training, can help mitigate the risk of falling victim to ChamelDoH and similar threats.
If you found these security learnings valuable, don’t miss out on more exclusive content. Follow us on Twitter and Instagram to stay informed about emerging threats and developments.
Check out the Cyber Safety Section and Subscribe our Newsletter, Join our community and gain access to the latest cybersecurity trends to bolster your defense against evolving threats & associated risks😇



