In a recent discovery, cybersecurity researchers have uncovered a sophisticated rootkit that has been signed by Microsoft. This Microsoft signed rootkit is specifically designed to establish communication with an attack infrastructure controlled by malicious actors. The analysis suggests that the same group responsible for the previously identified FiveSys rootkit, which emerged in October 2021, is behind this latest activity.
The primary targets of these Chinese hackers are gaming companies within China. It is noteworthy that the malware managed to pass through the Windows Hardware Quality Labs (WHQL) process and obtain a valid signature.
Understanding the Rootkit
Multiple variants of the rootkit have been identified, spanning across eight different clusters. Shockingly, 75 drivers signed using Microsoft’s WHQL program in 2022 and 2023 have been discovered. Trend Micro’s analysis of some of the samples revealed debug messages in the source code, indicating that the operation is still in the development and testing phase.
Functionality and Operation
The initial stage of the rootkit involves disabling the User Account Control (UAC) and Secure Desktop mode by modifying the registry. Additionally, it initializes Winsock Kernel (WSK) objects to establish network communication with a remote server. The rootkit periodically polls the server to retrieve more payloads, which are then decoded, decrypted, and loaded directly into memory. This process allows the rootkit to function as a stealthy kernel driver loader, effectively bypassing detection mechanisms.
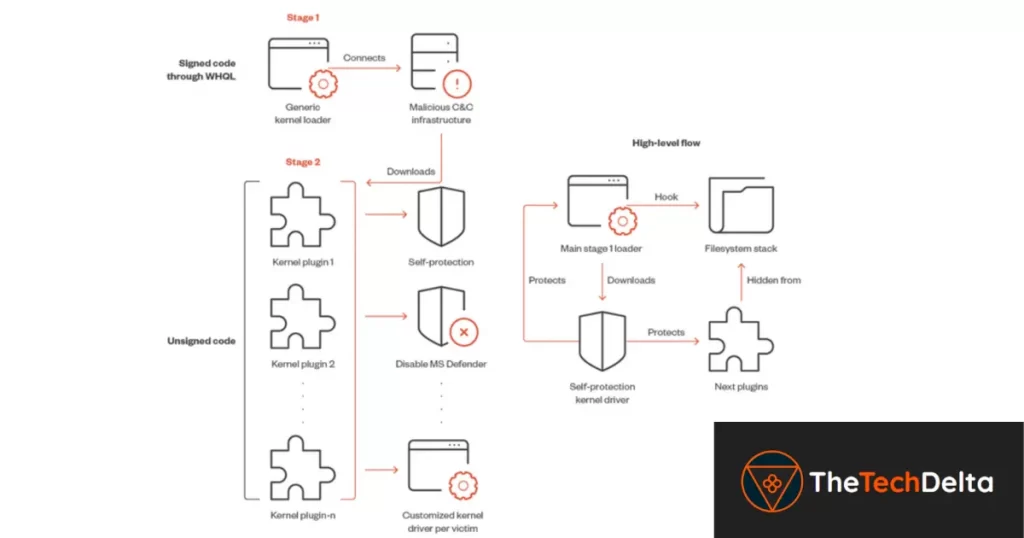
The rootkit’s main binary acts as a universal loader, enabling the attackers to load a second-stage unsigned kernel module. Each plug-in within the second-stage is customized to the victim’s machine, with some even containing a custom compiled driver for each specific system. These plug-ins are equipped with diverse capabilities, including achieving persistence, disarming Microsoft Defender Antivirus, and deploying a proxy server to redirect web browsing traffic.
Microsoft Signed Rootkit Phenomenon
Similar to the FiveSys rootkit, the new rootkit detections have been primarily limited to China. One of the suspected entry points for these infections is believed to be a trojanized Chinese game. Cisco Talos had previously discovered a malicious driver called RedDriver, which aligns with these findings. Reports from Cisco Talos and Sophos highlight the use of Microsoft-signed malicious kernel-mode drivers by Chinese-speaking threat actors, who leverage open-source software popular in the video game cheat development community to bypass Microsoft’s restrictions.
A Troubling Reality
Researchers have identified a staggering 133 malicious drivers signed with legitimate digital certificates, with 81 of them capable of terminating antivirus solutions on victims’ systems. The remaining drivers function as rootkits, covertly monitoring sensitive data transmitted over the internet. The fact that these drivers are signed by the Windows Hardware Compatibility Program (WHCP) enables attackers to install them on compromised systems without raising any alarms, allowing them to carry out malicious activities without significant hindrance.
“Because drivers often communicate with the ‘core’ of the operating system and load before security software, when they are abused, they can be particularly effective at disabling security protections – especially when signed by a trusted authority,” Christopher Budd, director of threat research at Sophos X-Ops, said.
Response from Microsoft
In response to these disclosures, Microsoft has implemented blocking protections and suspended the seller accounts of the partners involved in the incident. These measures aim to safeguard users from future threats and mitigate the impact of these rootkits. The discovery sheds light on an evolving attack vector that adversaries actively exploit to gain privileged access to Windows machines while evading detection by security software.
Conclusion
The emergence of a Microsoft-signed rootkit used by Chinese hackers to target the gaming sector in China reveals the ever-evolving nature of cyber threats. Rootkits continue to be employed by malicious actors to conceal their malicious code, compromise security measures, and operate undetected for prolonged periods.
The research underscores the necessity for constant vigilance and advanced security measures to combat sophisticated threat actors. As technology advances, it becomes crucial to stay informed and adopt robust cybersecurity practices to protect sensitive data and prevent future cyberattacks.
As the cybersecurity landscape continues to evolve, it is essential to stay informed about emerging threats and developments. I would highly suggest you to visit our CyberSecurity section to enhance your defenses and stay ahead of evolving cyber threats.
If you found these cybersecurity updates valuable, don’t miss out on more exclusive content. Follow us on Twitter and Instagram to stay informed about emerging threats and developments. Join our community and gain access to the latest cybersecurity trends to bolster your defense against evolving risks.



