The CoralRaider Malware is behind a recent surge in malicious activity, revealing an ongoing campaign targeting users across various regions.
Spearheaded by a group identified as CoralRaider, this campaign has been observed distributing multiple information-stealing malware, including CryptBot, LummaC2, and Rhadamanthys.
Notably, these malware strains are hosted on Content Delivery Network (CDN) cache domains, indicating a sophisticated approach to evasion and propagation.
Exploiting the infrastructure of CDN cache domains underscores the intricate tactics employed by CoralRaider, highlighting the complexity of their operation and the challenges in combating such cyber threats effectively.
Identification of CoralRaider Malware
Cisco Talos, a leading cybersecurity firm, has connected this campaign to CoralRaider with a moderate level of confidence. This group, suspected to originate from Vietnam, gained attention recently due to its involvement in cyber operations.
Talos’ analysis draws parallels between this campaign and CoralRaider’s previous activities, particularly the Rotbot campaign, highlighting similarities in tactics, techniques, and procedures (TTPs).
The correlation between this ongoing campaign and CoralRaider’s operations underscores the persistent threat posed by this group. Suspected to have its origins in Vietnam, CoralRaider’s recent prominence in cyber operations has raised significant concerns among cybersecurity experts.
Talos’ in-depth examination of the current campaign reveals striking resemblances to CoralRaider’s past endeavors, particularly their Rotbot campaign.
This pattern of similarity reinforces the notion that CoralRaider operates with a distinct modus operandi, characterized by specific tactics, techniques, and procedures.
Scope of the Campaign
The targets of this malicious endeavor span diverse business sectors and geographical locations, including but not limited to the United States, Nigeria, Pakistan, and Germany. Such widespread targeting raises concerns about the potential impact on global cybersecurity.
This broad scope of victims underscores the far-reaching implications of CoralRaider’s activities, amplifying the urgency for enhanced cybersecurity measures worldwide.

Modus Operandi
The attack chain primarily relies on users unknowingly downloading malicious files disguised as movie files via web browsers.
These files serve as conduits for the malware, hinting at the possibility of a large-scale assault. CoralRaider employs a CDN cache to store these malicious files, enabling quick and efficient distribution while evading detection by network defenses.
This strategic use of CDN cache enhances the speed and efficacy of malware dissemination, presenting formidable challenges for cybersecurity professionals striving to detect and mitigate such threats effectively.
Technical Details
The initial access point for victims is suspected to be phishing emails containing deceptive links leading to ZIP archives housing Windows shortcut (LNK) files.
These shortcuts execute PowerShell scripts, fetching HTML application (HTA) payloads from the CDN cache. Subsequently, these payloads execute JavaScript code, initiating the deployment of an embedded PowerShell loader.
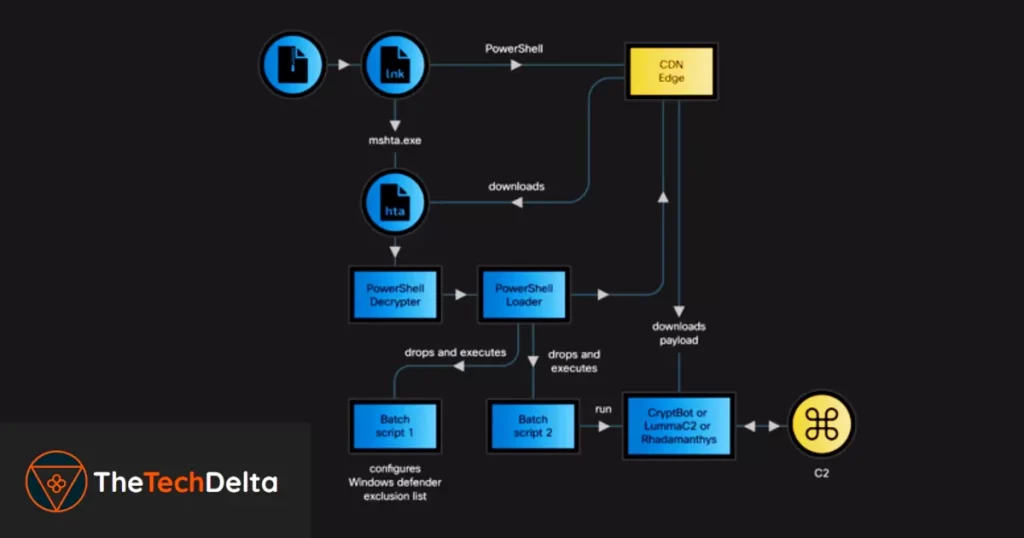
This loader, equipped with evasion techniques, facilitates the download and execution of one of the three information-stealing malware variants.
This intricate process underscores the sophisticated tactics employed by CoralRaider, demonstrating their adeptness at circumventing traditional security measures to infiltrate systems and compromise sensitive data.
Impact of the Malware
Once deployed, the malware extracts a plethora of sensitive information from the victim’s system, including browser data, credentials, cryptocurrency wallets, and financial details.
Notably, an updated version of CryptBot deployed in this campaign includes advanced anti-analysis measures, demonstrating the adaptability and sophistication of CoralRaider’s operations.
The inclusion of such measures signifies the continuous evolution of CoralRaider’s tactics, underscoring the ongoing challenge posed to cybersecurity professionals in safeguarding against their malicious activities.
Conclusion
The CoralRaider malware campaign represents a significant threat to cybersecurity, leveraging advanced techniques to infiltrate systems and steal sensitive information.
Organizations and individuals are urged to remain vigilant against phishing attempts and ensure robust cybersecurity measures are in place to mitigate the risks posed by such malicious activities.
If you found these security learnings valuable, don’t miss out on more exclusive content. Follow us on Twitter and Instagram to stay informed about emerging threats and developments.
Check out the Cyber Safety Section and Subscribe our Newsletter, Join our community and gain access to the latest cybersecurity trends to bolster your defense against evolving threats & associated risks 🙂