Venturing into the world of cybersecurity, Governance, Risk, and Compliance (GRC) may not initially spark excitement. Yet, its pivotal role in holistic business safeguarding cannot be overstressed 💯
This exploration aims to illuminate the vibrant synergy between GRC and cybersecurity, revealing the intricate ways in which they mutually reinforce one another, creating a robust shield for businesses.
Let’s delve into the intricacies of this crucial partnership, unraveling the profound impact it has on ensuring the security and resilience of modern enterprises.
- Cybersecurity in Today’s Landscape
- Decoding GRC – A Pillar of Business Resilience
- GRC’s Pivotal Role in Cybersecurity
- Technical Benefits of GRC in Boosting Cybersecurity
- The Integration Imperative – GRC and Cybersecurity Unite
- Empowering Cybersecurity Through GRC – The Methodology
- The Capability Model – Unraveling the Steps
- Conclusion – A Unified Future for Business Security
- FAQs
Cybersecurity in Today’s Landscape
In our increasingly interconnected world, cybersecurity stands as the safeguard against cyber threats. This protection becomes more challenging due to factors like global connectivity, hybrid work models, and the surge in cloud services. In essence, cybersecurity is not just crucial; it has become indispensable for the sustained operation of any organization.
Decoding GRC – A Pillar of Business Resilience
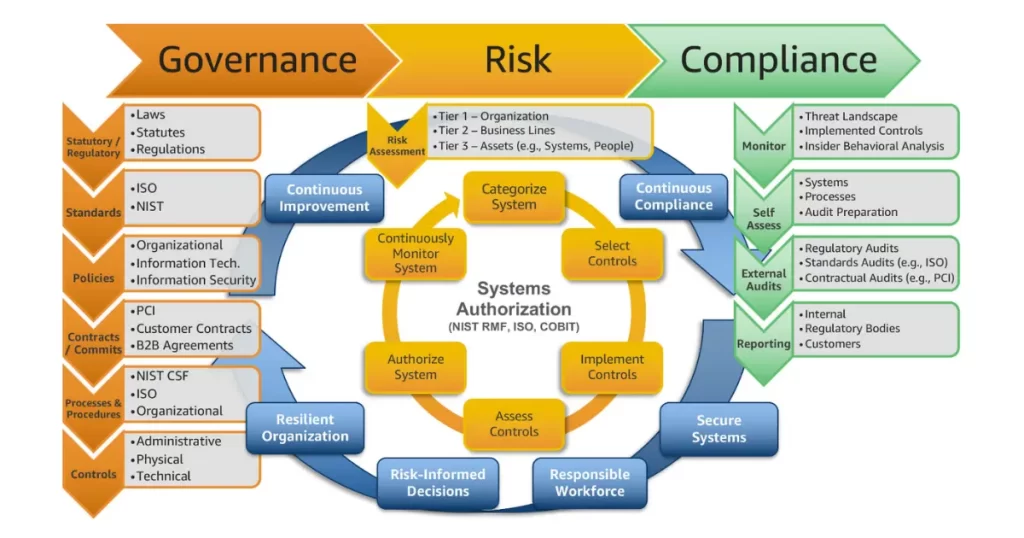
Governance, Risk, and Compliance (GRC) act as the strategic framework for managing a company’s governance, risk management, and compliance with regulations. From a cybersecurity perspective, GRC aligns IT operations with business goals, ensuring adherence to best practices, policies, and regulations. It’s not just a set of rules; it’s a culture builder, fostering trust and efficiency within the organization.
GRC’s Pivotal Role in Cybersecurity
Leveraging GRC empowers your business to craft and oversee tailored policies, ensuring the secure handling and protection of vital company data.
To achieve robust cybersecurity, organizations must align people, systems, and technologies with business goals. GRC facilitates this alignment, playing a critical role in various aspects:
Roles and Responsibilities – Enhancing Communication and Accountability
Assigning clear roles and responsibilities fosters improved communication across business units, cultivating a culture of accountability and collaboration. This strategic alignment ensures that everyone contributes effectively to cybersecurity initiatives.
Risk Mitigation – Comprehensive Support for Internal and External Efforts
Empowering both internal and external risk mitigation efforts, this crucial aspect of cybersecurity strategy involves proactive measures and strategic planning. By comprehensively addressing potential risks, organizations can fortify their defenses and enhance overall resilience.
Unified Vocabulary – Building Consistency Across Teams and Departments
Creating and maintaining a unified vocabulary across departments and teams is essential for fostering consistency in communication. This practice promotes a shared understanding of cybersecurity concepts and facilitates more effective collaboration, minimizing the risk of miscommunication.
Data Manipulation Procedures – Safeguarding Information with Secure Practices
Assisting in the implementation of secure data manipulation practices, this aspect of cybersecurity ensures that information is handled with the utmost security. By following established procedures, organizations can safeguard sensitive data, maintaining the integrity and confidentiality of crucial information.
Standardizing Best Practices – Cultivating a Unified Approach for Security
Establishing a unified approach for everyone to act securely and with integrity is a cornerstone of cybersecurity. Standardizing best practices ensures that employees across the organization are aligned in their actions, promoting a culture of security and adherence to cybersecurity guidelines.
Regulatory Compliance – Navigating Industry and Government Regulations
Ensuring adherence to industry and government regulations is paramount for organizations. This involves staying informed about evolving compliance requirements and implementing measures to meet these standards. A proactive approach to regulatory compliance safeguards the organization’s reputation and minimizes legal risks.
Audit Support – Ensuring Transparency with Internal Audits
Facilitating internal audits and continuous control monitoring supports transparency and accountability. By maintaining a proactive stance towards audits, organizations demonstrate their commitment to cybersecurity best practices, providing stakeholders with assurance and confidence in their security measures.
With GRC Effortlessly administer and monitor individual policies, guaranteeing proper distribution and acknowledgment.
Technical Benefits of GRC in Boosting Cybersecurity
The technical benefits of GRC in the realm of cybersecurity are manifold:
Risk Mitigation – Strategic Understanding and Addressing of Cybersecurity Risks
Empowering organizations to comprehend and confront cybersecurity risks, GRC plays a pivotal role in developing comprehensive mitigation plans. This strategic approach ensures a proactive stance towards potential threats, fortifying the organization’s overall security posture.
Data Privacy – Navigating Privacy Regulations for Customer and Employee Data Safeguarding
GRC assists organizations in navigating the complexities of privacy regulations, particularly in safeguarding sensitive customer and employee data. This ensures adherence to privacy standards, fostering trust and compliance with evolving data protection requirements.
Audit Support – Structured Approach for Accountability in Internal Audits
GRC provides a structured approach to creating and maintaining audit materials, fostering transparency and accountability. This systematic process ensures that internal audits are conducted with precision, showcasing the organization’s commitment to rigorous cybersecurity practices.
Visibility – Comprehensive Insight into Security Compliance Programs
GRC’s integrated approach offers unparalleled visibility into every facet of security compliance programs. This comprehensive insight enables organizations to proactively address potential vulnerabilities and make informed, data-driven decisions to enhance their overall security posture.
Regulatory Compliance – Staying Ahead of Evolving Regulations with GRC
Keeping organizations abreast of evolving regulations, GRC aids in compliance management. This proactive approach ensures that organizations stay ahead of regulatory changes, enabling them to adapt policies and practices to meet the latest industry and government standards.
Third-Party Vendor Selection – Ensuring Secure Partnerships with GRC Assistance
GRC aids in selecting and vetting third-party vendors, ensuring secure partnerships. This strategic support extends to evaluating corporate reputation, financials, network security, and other critical factors, ensuring that vendors align with stringent cybersecurity standards.
The Integration Imperative – GRC and Cybersecurity Unite
Integrating GRC and cybersecurity is not just an option; it is imperative for a successful and sustainable security strategy. This integration offers benefits such as:
Enhanced Security Posture – Comprehensive Overview of Organizational Security
Achieving a comprehensive view of the organization’s security posture is a pivotal outcome of strategic cybersecurity measures. This holistic approach ensures a thorough understanding of vulnerabilities and strengths, leading to enhanced overall security resilience.
Leadership Support – Garnering Support Through Clear and Comprehensive Security Storytelling
Gaining support from leadership is vital for a robust cybersecurity strategy. Conveying a clear and comprehensive security story ensures that leaders understand the significance of cybersecurity initiatives, fostering support and commitment to prioritizing security measures.
Improved Communication – Facilitating Swift Communication and Collaborative Decision-Making
Facilitating faster communication, congruent metrics, and collaborative decision-making is a cornerstone of effective cybersecurity strategies. By streamlining communication processes and ensuring consistent metrics, organizations can enhance their ability to make informed decisions and respond promptly to security challenges.
Reduced Costs – Minimizing Manual Input and Errors for Operational Efficiency
Minimizing manual input and human errors is a key strategy for reducing operational costs in cybersecurity. By implementing efficient processes and automation, organizations can optimize their resources and minimize the risk of costly errors, ensuring a more cost-effective cybersecurity approach.
Empowering Cybersecurity Through GRC – The Methodology
The Open Compliance and Ethics Group (OCEG) has devised a Capability Model, an open-source methodology merging governance, risk, audit, compliance, ethics/culture, and IT into a unified approach. This model enables organizations to document best practices, unifying vocabulary, defining common components, and promoting standardized practices.
The Capability Model – Unraveling the Steps
Learn – Strategic Understanding of Business Culture, Stakeholders, and Goals
During the “Learn” phase, the focus is on obtaining a comprehensive understanding of business culture, stakeholders, and goals. This strategic knowledge serves as the foundation for guiding strategy and objectives, ensuring alignment with the organization’s overarching mission and vision.
Align – Strategic Unification of Objectives, Stakeholder Expectations, and Resource Planning
In the “Align” phase, the emphasis is on strategically unifying organizational objectives with stakeholder expectations. This involves aligning executives with stakeholders’ expectations and meticulously planning resource allocation. This integrated approach ensures that organizational goals are in harmony with the expectations of key stakeholders.
Perform – Proactive Implementation of Controls, Policies, and Risk Mitigation
The “Perform” phase is characterized by the proactive implementation of controls, policies, and risk mitigation strategies. This includes the execution of measures to safeguard the organization against potential threats while continuously monitoring for timely issue detection. This operational phase ensures a vigilant and responsive cybersecurity strategy.
Review – Continuous Evaluation for Enhanced Strategy Design and Operational Performance
In the “Review” phase, there is a continuous evaluation of the design and operational performance of the cybersecurity strategy. This critical assessment fosters a culture of continuous improvement, allowing organizations to adapt and enhance their strategies in response to evolving cyber threats and technological landscapes.
Conclusion – A Unified Future for Business Security
In conclusion, GRC and cybersecurity are not standalone entities but interwoven threads vital for an organization’s resilience. Their integration is not just a strategic move but a necessity in navigating the complex landscape of modern cyber threats.
As we move forward, the harmonious collaboration of GRC and cybersecurity will undoubtedly be the cornerstone of a secure, thriving business future.
If you found these security learnings valuable, don’t miss out on more exclusive content. Follow us on Twitter and Instagram to stay informed about emerging threats and developments.
Check out the Cyber Safety Section and Subscribe our Newsletter to Join our community and gain access to the latest cybersecurity trends to bolster your defense against evolving risks🔥
FAQs
What is GRC in Cyber Security?
GRC in Cyber Security stands for Governance, Risk, and Compliance. It is a strategic framework for managing overall governance, enterprise risk management, and regulatory compliance within the realm of cybersecurity.
What Does GRC Mean in Cyber Security?
In Cyber Security, GRC means Governance, Risk, and Compliance. GRC is a comprehensive approach to aligning IT operations with business objectives, effectively managing risks, and ensuring regulatory compliance in the cybersecurity domain.
What is GRC Cyber Security?
GRC and Cyber Security refers to the integration of Governance, Risk, and Compliance principles in the field of cybersecurity. It involves implementing best practices, policies, and procedures to align IT with business goals, manage risks, and ensure regulatory compliance for enhanced security.
What Are the Key Components of GRC in Cyber Security?
The key components of GRC in Cyber Security include governance, which guides decision-making; risk management, addressing potential threats; and compliance, ensuring adherence to regulations for robust cybersecurity.
How Does GRC Contribute to Cyber Security Resilience?
GRC contributes to Cyber Security resilience by providing a structured approach to aligning IT with business objectives, fostering a culture of compliance, and effectively managing risks. This integrated strategy enhances an organization’s ability to withstand and respond to cyber threats.
Why is GRC Important in the Cyber Security Landscape?
GRC is crucial in the Cyber Security landscape as it establishes a framework for organizations to proactively manage risks, adhere to regulations, and align IT operations with overarching business goals. This comprehensive approach is essential for building a resilient and secure cyber environment.
How Does GRC Facilitate Communication and Collaboration in Cyber Security?
GRC facilitates communication and collaboration in Cyber Security by standardizing best practices, creating a unified vocabulary, and assigning clear roles and responsibilities. This ensures a cohesive approach, minimizing miscommunication and enhancing overall effectiveness in addressing cybersecurity challenges.
What Role Does GRC Play in Data Protection Within Cyber Security?
In Cyber Security, GRC plays a vital role in data protection by implementing and managing policies and procedures. It ensures the secure manipulation of data, adherence to privacy regulations, and the establishment of a unified approach to safeguarding sensitive customer and employee information.



