A critical flaw in Microsoft Defender SmartScreen, now patched, has been exploited in a new cyber campaign aimed at distributing various information stealers, including ACR Stealer, Lumma, and Meduza.
This security vulnerability, identified as CVE-2024-21412 with a CVSS score of 8.1, has raised significant concerns among cybersecurity professionals and enthusiasts.
The exploitation of this flaw has underscored the persistent threat posed by cybercriminals who continually adapt their methods to bypass security measures.
The attackers have demonstrated a sophisticated understanding of the Defender SmartScreen, enabling them to effectively deliver their malicious payloads without detection.
This development has led to a heightened state of alert within the cybersecurity community as experts work to understand the full extent of the threat and develop robust countermeasures.
The ability of these information stealers to infiltrate and extract sensitive data from various platforms, including web browsers, crypto wallets, and messaging apps, signifies a critical escalation in the tactics employed by cyber adversaries.
This ongoing situation calls for an urgent reassessment of current cybersecurity protocols to ensure that systems remain secure against such advanced threats.
Campaign Targeting and Exploitation of Microsoft Defender
Fortinet FortiGuard Labs detected this stealer campaign targeting users in Spain, Thailand, and the United States.
The attackers utilized malicious files to exploit the high-severity vulnerability, bypassing SmartScreen protection to deliver their malicious payloads. Microsoft addressed this issue in their February 2024 security updates.
Attack Methodology
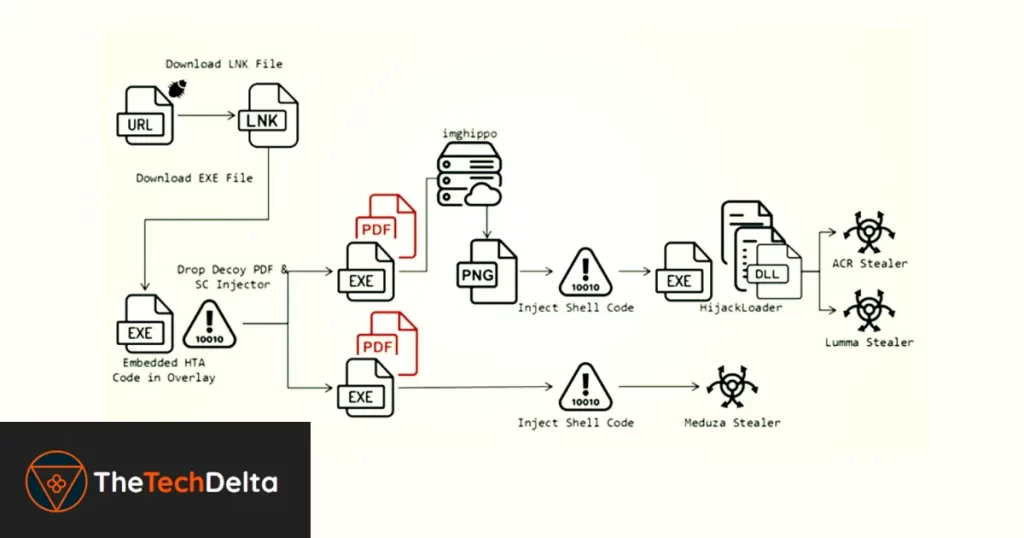
Initial Attack Vector
Security researcher Cara Lin explains that the attack begins with victims being lured into clicking a specially crafted link leading to a URL file.
This URL file is designed to download an LNK file, which subsequently downloads an executable file containing an HTML Application (HTA) script.
Payload Deployment
The HTA file plays a crucial role in decoding and decrypting PowerShell code, which then fetches a decoy PDF file and a shellcode injector.
This process ultimately leads to the deployment of Meduza Stealer or Hijack Loader, which then launches ACR Stealer or Lumma.
Details of the Stealers
ACR Stealer
ACR Stealer, considered an evolved version of GrMsk Stealer, was advertised in late March 2024 by a threat actor named SheldIO on the Russian-language underground forum RAMP.
This stealer uses a dead drop resolver (DDR) technique on the Steam community website to hide its command-and-control (C2) infrastructure. It can extract information from web browsers, cryptocurrency wallets, messaging apps, FTP clients, email clients, VPN services, and password managers.
Lumma Stealer
Recent attacks involving Lumma Stealer have also been observed using similar techniques, allowing adversaries to change C2 domains easily, thus making their infrastructure more resilient.
The AhnLab Security Intelligence Center (ASEC) has highlighted the increased adaptability and persistence of such attacks.
Meduza Stealer
Meduza Stealer is another significant threat in this campaign, following similar attack vectors and payload delivery methods to compromise user data and system integrity.
Emergence of New Threats
CrowdStrike has disclosed that threat actors are exploiting a recent Windows outage to distribute a new information stealer called Daolpu. This attack involves a macro-laced Microsoft Word document, disguised as a Microsoft recovery manual, to activate the infection process.
Once the DOCM file is opened, it retrieves a second-stage DLL file from a remote server, launching Daolpu to harvest credentials and cookies from various web browsers.
The cybersecurity landscape is also seeing the rise of new stealer malware families like Braodo and DeerStealer. Cybercriminals are increasingly using malvertising techniques, promoting legitimate software such as Microsoft Teams to deploy malware like Atomic Stealer.
Conclusion
The exploitation of the Microsoft Defender SmartScreen vulnerability underscores the ever-evolving tactics of cybercriminals.
As they ramp up their distribution campaigns, it becomes increasingly perilous to download applications via search engines.
Users must navigate between malvertising and SEO poisoning, making it imperative to remain vigilant and employ robust cybersecurity measures.
The continuous emergence of new malware families and sophisticated attack vectors highlights the critical need for timely updates and comprehensive security practices.
If you found these security learnings valuable, don’t miss out on more exclusive content. Follow us on Twitter and Instagram to stay informed about emerging threats and developments.
Check out the Cyber Safety Section and Subscribe our Newsletter, Join our community and gain access to the latest cybersecurity trends to bolster your defense against evolving threats & associated risks 🙂



