A newly discovered malware campaign is aggressively targeting publicly exposed Docker API endpoints, aiming to deliver cryptocurrency miners and other malicious payloads.
This sophisticated attack leverages vulnerabilities in Docker configurations, allowing cybercriminals to infiltrate systems, gain unauthorized access, and deploy harmful software.
The primary objective of these attackers is to exploit computational resources for cryptojacking, significantly impacting system performance and security.
This latest threat underscores the critical need for robust security measures, such as regularly updating Docker configurations, implementing strict access controls, and continuously monitoring network activities, to protect Docker environments from such cyberattacks and ensure overall system integrity.
Also Read : Critical Security Vulnerability in GitHub Enterprise Server – Authentication Bypass Flaw
Detailed Analysis of the Malware Campaign
Let’s understand the intricacies of the malware campaign, highlighting the sophisticated tools and techniques employed by the attackers.
It examines the initial attack vectors, payload deployment methods, and advanced obfuscation tactics.
The analysis underscores the campaign’s complexity and the persistent threat it poses to exposed Docker environments.
Tools and Techniques
Cybersecurity researchers have identified several sophisticated tools utilized in this campaign. Among these are a remote access tool capable of downloading and executing additional malicious programs, and a utility designed to propagate the malware via SSH.
The campaign has shown tactical overlaps with the previous Spinning YARN activity, which targeted misconfigured Apache Hadoop YARN, Docker, Atlassian Confluence, and Redis services for cryptojacking purposes.
Initial Attack Vector in Exposed ports of Docker Servers
The attack begins with threat actors scanning for Docker servers with exposed ports, particularly port 2375. Once identified, they engage in a series of steps starting with reconnaissance to gather information about the target system.
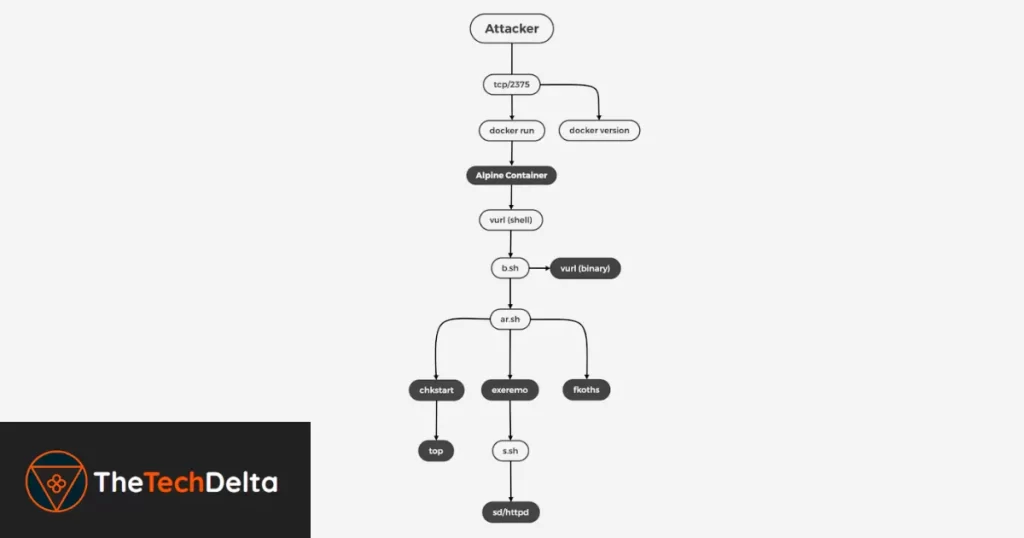
This is followed by privilege escalation, which allows them to gain higher-level access, and finally the exploitation phase where the malicious payloads are deployed.
Payload Deployment
The primary method of payload deployment involves executing a shell script named “vurl.” This script downloads another script called “b.sh,” which contains a Base64-encoded binary also named “vurl.”
The “b.sh” script decodes this binary and places it in the /usr/bin directory, replacing the original shell script version.
This binary variant uses hard-coded command-and-control (C2) domains to communicate with the attackers’ infrastructure.
Advanced Malware Features
Another crucial script in this campaign is “ar.sh,” which performs several actions, such as creating a working directory, installing tools to scan the internet for vulnerable hosts, disabling firewalls, and fetching subsequent payloads, notably “chkstart.”
This payload, a Golang binary, configures the host for remote access and downloads additional tools like “m.tar” and “top,” with the latter being an XMRig miner.
Obfuscation and Persistence Mechanisms
In a bid to complicate analysis, much of the functionality that was previously handled by shell scripts in the Spinning YARN campaign has now been ported to Golang binaries.
This move significantly hinders static analysis, making it more challenging for cybersecurity experts to dissect and understand the malware’s behavior.
Spread and Infiltration
The malware also includes components designed to spread the infection to other hosts. One such tool is “exeremo,” which enables lateral movement and further dissemination of the malware.
Additionally, “fkoths,” a Go-based ELF binary, is deployed to erase traces of malicious activity and resist forensic analysis efforts.
Infection and Scanning
“Exeremo” deploys a shell script (“s.sh”) responsible for installing various scanning tools such as pnscan, masscan, and a custom Docker scanner (“sd/httpd”).
These tools are used to identify and flag other vulnerable systems, thereby widening the scope of the attack.
Conclusion
The ongoing evolution of this malware campaign highlights the persistent threats targeting misconfigured Docker hosts. The shift to Golang binaries for critical functions indicates a deliberate attempt by the threat actors to complicate detection and analysis processes.
To mitigate these risks, organizations must ensure their Docker configurations are secure, regularly updated, and monitored for suspicious activities. Adopting comprehensive cybersecurity practices is essential in defending against these sophisticated and evolving threats.
If you found these security learnings valuable, don’t miss out on more exclusive content. Follow us on Twitter and Instagram to stay informed about emerging threats and developments.
Check out the Cyber Safety Section and Subscribe our Newsletter, Join our community and gain access to the latest cybersecurity trends to bolster your defense against evolving threats & associated risks 🙂



