Have you heard of Phishing as a Service, or PhaaS 🤔
It’s like a modern twist on traditional phishing attacks, but with a business model.
It’s like a situation where less experienced hackers now have the chance to run multiple phishing campaigns without needing advanced technical skills. How? Well, with PhaaS, they can access ready-made phishing kits, think fake websites, phishing pages, and more but for a fee.
So, what’s the deal with Phishing as a Service (PhaaS) ?
It’s basically a service where cybercriminals act as providers, offering tools and know-how for phishing attacks. This means even beginners can jump into the game and launch their own attacks, thereby increasing the risk to a next level for cyber criminal activities.
In this article, I’ll break down what exactly Phishing as a Service is, why it’s a big deal for businesses, and most importantly, how you can shield your organization from falling victim to it ✌🏻
- Phishing – The Deceptive Technique
- The Mechanics Behind Phishing as a Service (PhaaS)
- The Growing Threat to Organizations
- Greatness Platform – Phishing as a Service for Microsoft 365 Users
- Challenges in Combatting Phishing as a Service (PhaaS)
- Effective Strategies for Mitigating Phishing Risks
- Identifying Red Flags and Safeguarding Against Phishing
- Conclusion
Phishing – The Deceptive Technique
Phishing itself is a malicious technique aimed at deceiving individuals into divulging sensitive information, such as login credentials and personal data.

Phishing as a Service (PhaaS) simplifies this process by offering ready-made phishing kits, complete with email templates, fake website templates, and target lists, thereby enabling even novices to execute sophisticated attacks.
The Mechanics Behind Phishing as a Service (PhaaS)
Operating on a software-as-a-service (SaaS) model, Phishing as a Service (PhaaS) provides comprehensive tools for cybercriminals to execute attacks with ease.

These kits not only facilitate phishing campaigns but also allow hackers to profit by selling stolen data or using it for future malicious activities.
The Growing Threat to Organizations
Phishing as a Service (PhaaS) poses a significant threat to organizations worldwide, as evidenced by its increasing prevalence.
According to the FBI’s Internet Crime Report, phishing remains one of the most common cybercrimes, resulting in substantial financial losses.
The accessibility and affordability of PhaaS have democratized cybercrime, making it accessible to a broader range of malicious actors.
Greatness Platform – Phishing as a Service for Microsoft 365 Users
One notable platform in this arena is Greatness, which exclusively targets business users of Microsoft 365 cloud services.
Greatness equips cybercriminals with sophisticated tools, including attachment and link builders, to craft convincing decoy and login pages.
These meticulously designed pages, adorned with authentic company logos and pre-filled email addresses, have primarily targeted industries such as manufacturing, healthcare, and technology across various regions.

These pages, adorned with authentic company logos and pre-filled email addresses, have primarily targeted manufacturing, healthcare, and technology sectors across various regions.
Challenges in Combatting Phishing as a Service (PhaaS)
Despite its growing prevalence, combating PhaaS presents unique challenges for cybersecurity professionals.
Unlike traditional phishing attacks, PhaaS-generated campaigns can be highly convincing, thanks to advancements in AI technology.
To mitigate these risks, organizations must adopt proactive measures, including email scrutiny, awareness training, and deploying advanced anti-phishing solutions.
Effective Strategies for Mitigating Phishing Risks
Protecting against Phishing as a Service (PhaaS) requires a multifaceted approach that combines technology, education, and vigilance. Some effective strategies include Email Content Verification, Credential Protection, Multi-Factor Authentication (MFA), Anti-Phishing Solutions, Awareness Training. Lets try to understand each one of them below.
Email Content Verification
Encourage employees to scrutinize email content thoroughly, including sender information, links, and attachments, to ensure authenticity and mitigate risks associated with phishing attacks and malware infections.
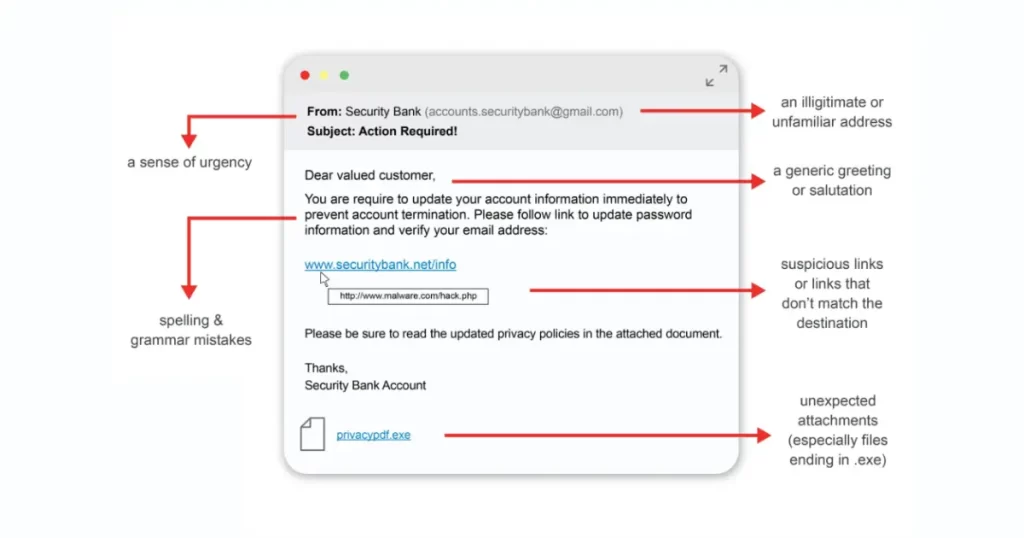
The depicted image ☝🏻 highlights crucial parameters to inspect when encountering a suspicious email.
Credential Protection
Remind users to safeguard their login credentials and sensitive information, refraining from sharing passwords or financial details in response to unsolicited requests.
Multi-Factor Authentication (MFA)
Enhance security measures by implementing MFA, requiring additional verification steps beyond passwords to access sensitive systems or data.
Anti-Phishing Solutions
Implement advanced anti-phishing technologies, leveraging machine learning and natural language processing to detect and block malicious emails before they reach users’ inboxes.
Awareness Training
Educate employees about common phishing tactics, emphasizing the importance of identifying suspicious emails and avoiding disclosing sensitive information.
Identifying Red Flags and Safeguarding Against Phishing
Despite proactive measures, users may still encounter phishing attempts.
It’s essential to remain vigilant and watch out for common red flags, such as requests for sensitive information, suspicious sender domains, or a sense of urgency being created.
By implementing a combination of technical solutions, employee education, and proactive monitoring, businesses can safeguard against PhaaS-driven phishing attacks and protect sensitive data and assets.
Conclusion
As PhaaS continues to evolve, organizations must adapt their cybersecurity strategies to counter emerging threats effectively.
By implementing robust defense mechanisms, fostering a culture of cybersecurity awareness, and leveraging advanced technologies, businesses can mitigate the risks posed by PhaaS-driven phishing attacks.
Through proactive measures and ongoing vigilance, organizations can safeguard their data, assets, and reputation in the face of evolving cyber threats.
If you found these security learnings valuable, don’t miss out on more exclusive content. Follow us on Twitter and Instagram to stay informed about emerging threats and developments.
Check out the Cyber Safety Section and Subscribe our Newsletter, Join our community and gain access to the latest cybersecurity trends to bolster your defense against evolving threats & associated risks🙂




You need to take part in a contest for one of the highest quality websites on the web.
I will highly recommend this site 🙂
Hey Ryder.. Thank you so much for the kind words.