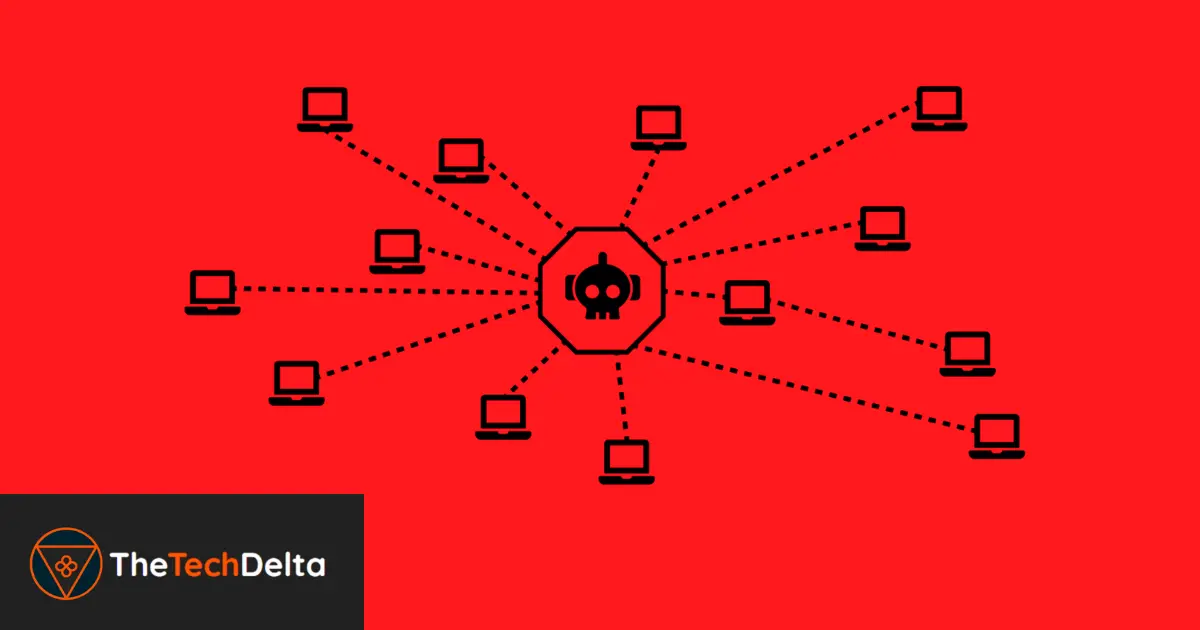
A newly discovered botnet, dubbed Raptor Train, has compromised over 200,000 small office/home office (SOHO) and Internet of Things (IoT) devices globally 😟
The botnet, believed to be operated by a Chinese state-sponsored group known as Flax Typhoon (also referred to as Ethereal Panda or RedJuliett), has raised significant concerns in the cybersecurity community.
The growing scale and sophistication of this botnet indicate a major threat to both private and governmental entities worldwide.
Botnet Overview and Operation
Raptor Train has been operational since May 2020, peaking in activity with 60,000 compromised devices by mid-2023.
Since then, it has expanded to infect a wide range of SOHO routers, network video recorders (NVRs), digital video recorders (DVRs), network-attached storage (NAS) devices, and IP cameras, all across the globe.
This botnet operates through a three-tiered structure:
- Tier 1: Compromised IoT devices such as routers, IP cameras, and NAS systems.
- Tier 2: Servers dedicated to exploitation, command-and-control (C2) operations, and payload delivery.
- Tier 3: Centralized management nodes using an Electron-based front-end application named “Sparrow” (also known as Node Comprehensive Control Tool or NCCT).
Bot tasks are initiated from Tier 3 and routed through the C2 servers (Tier 2) before being sent to the compromised IoT devices (Tier 1). This multi-tiered architecture allows for widespread exploitation and coordination of malicious activities.
Devices and Geographic Spread
The botnet targets devices from well-known manufacturers, including ASUS, Hikvision, Mikrotik, TP-LINK, and Zyxel, among others.
A large number of the compromised devices are located in countries such as the U.S., Taiwan, Vietnam, Brazil, and Turkey, with most of these devices having an average lifespan of 17.44 days.
The lack of persistence mechanisms suggests that the attackers can quickly re-infect devices after reboots, leveraging a wide range of exploits available for various IoT devices.
Exploitation Techniques and Payload Delivery
Infected devices are compromised using an in-memory implant known as “Nosedive,” a custom variant of the Mirai botnet.
Nosedive is deployed via Tier 2 payload servers and is capable of executing commands, uploading and downloading files, and launching distributed denial-of-service (DDoS) attacks.
The Tier 2 servers rotate every 75 days to evade detection, while also acting as exploitation servers to recruit new devices into the botnet.
Evolution of Raptor Train
Since 2020, Raptor Train has been linked to four distinct campaigns, each characterized by different C2 domains and target devices:
- Crossbill Campaign (May 2020 – April 2022): Utilized the C2 domain k3121.com.
- Finch Campaign (July 2022 – June 2023): Utilized the C2 domain b2047.com.
- Canary Campaign (May 2023 – August 2023): Targeted ActionTec modems, Hikvision cameras, and ASUS routers.
- Oriole Campaign (June 2023 – September 2024): Utilized the C2 domain w8510.com, which gained prominence in the Cisco Umbrella domain rankings and Cloudflare Radar’s top 1 million domains.
These campaigns highlight the botnet’s ability to evolve and adapt, with the Canary campaign employing a multi-stage infection chain involving numerous bash scripts designed to download and execute malicious payloads at regular intervals.
The Growing Threat to Global Cybersecurity
Raptor Train has not been detected conducting DDoS attacks thus far, but it has been linked to the exploitation of critical sectors, including military, government, telecommunications, and higher education institutions.
The botnet has also been associated with scanning and exploitation attempts targeting Atlassian Confluence servers and Ivanti Connect Secure (ICS) appliances, suggesting a broad-scale reconnaissance effort by the attackers.
Links to Flax Typhoon
Evidence points to the involvement of Flax Typhoon, a Chinese threat actor with a history of targeting organizations across Taiwan, Southeast Asia, and North America.
The similarities in victim profiles, the use of Chinese-language tools, and the advanced tactics used by both Flax Typhoon and Raptor Train suggest a strong connection between the two entities.
Conclusion
The discovery of the Raptor Train botnet represents a growing cybersecurity threat, with its sophisticated architecture and widespread reach compromising over 200,000 devices globally.
This botnet’s ability to rapidly evolve and reinfect devices, coupled with its connections to a nation-state actor, underlines the urgent need for organizations to strengthen their security protocols.
As IoT devices become more ubiquitous, the risks posed by such botnets are likely to grow, making it crucial for individuals and businesses to remain vigilant and proactive in their cybersecurity efforts.
If you found these security learnings valuable, don’t miss out on more exclusive content. Follow us on Twitter and Instagram to stay informed about emerging threats and developments.
Check out the Cyber Safety Section and Subscribe our Newsletter, Join our community and gain access to the latest cybersecurity trends to bolster your defense against evolving threats & associated risks 🙂