Imagine your everyday messaging app morphing into a Trojan horse, silently delivering a multi-tool malware onto your device. Welcome to the unsettling reality of ToxicEye Malware, a RAT (Remote Access Trojan) that’s chillingly adept at blending in with the likes of your friendly neighborhood Telegram bot. This isn’t a dystopian future; it’s happening now, infiltrating organizations and personal devices with unsettling ease.
This isn’t a mere inconvenience. ToxicEye Malware is a cyber Swiss Army knife, capable of cleverly stealing passwords, recording your every keystroke, even capturing audio and video of your surroundings. The worst part? It’s whispering sweet nothings to its controllers through encrypted Telegram channels, leaving you utterly oblivious to the digital puppet master pulling the strings.
So, grab your digital coffee, because we’re about to unpack the chilling capabilities of ToxicEye, expose the cybercriminals’ playbook, and equip you with the knowledge to keep your data safe in this increasingly treacherous digital landscape.
- Telegram as a Covert Battlefield – The Cybersecurity Challenge
- Origins of ToxicEye Malware
- Telegram’s Anonymity Advantage and Global Accessibility
- ToxicEye’s Arsenal – Unleashing Havoc on Compromised Systems
- The Attack Chain Unraveled – From Telegram Bot to RAT Execution
- The Growing Trend – Telegram as an Out of the Box C2 System
- Conclusion
Telegram as a Covert Battlefield – The Cybersecurity Challenge
Telegram, known for its encrypted communication features, has become an unexpected battleground for cyber warfare. The researchers at Check Point have identified a staggering 130 attacks in the last three months alone, emphasizing the severity of the situation.
What makes this strategy even more insidious is the fact that hackers can execute malicious commands remotely, even if the Telegram app is neither installed nor actively used on the targeted systems.
Origins of ToxicEye Malware
ToxicEye, the malicious player in this cyber saga, operates as a versatile RAT, allowing cybercriminals to execute a myriad of attacks on compromised systems. Its deployment through phishing emails, concealing a malicious Windows executable file, marks the inception of a potential cyber threat.
As the toxic payload infiltrates systems, it establishes communication with a command-and-control (C2) server through Telegram, creating a covert channel for data exfiltration and manipulation.
Telegram’s Anonymity Advantage and Global Accessibility
One of the key strengths of this nefarious strategy lies in Telegram’s unique attributes. Unlike other communication platforms, Telegram remains unblocked by enterprise antivirus engines.
Moreover, the app’s registration process, which only requires a mobile number, facilitates anonymity for attackers. This anonymity, coupled with Telegram’s global accessibility, allows hackers to operate from virtually any location worldwide, evading security measures and heightening the challenge for cybersecurity professionals.
ToxicEye’s Arsenal – Unleashing Havoc on Compromised Systems
The ToxicEye malware isn’t just a one-trick pony; it boasts a comprehensive set of exploits, transforming compromised systems into cyber battlegrounds.
Among its capabilities are data theft, file transfer and deletion, process termination, keylogger deployment, and even the hijacking of a computer’s microphone and camera for audio and video surveillance.
To add to the menace, ToxicEye can encrypt files, holding them hostage for ransom, further escalating the potential damage inflicted on organizations.
The Attack Chain Unraveled – From Telegram Bot to RAT Execution
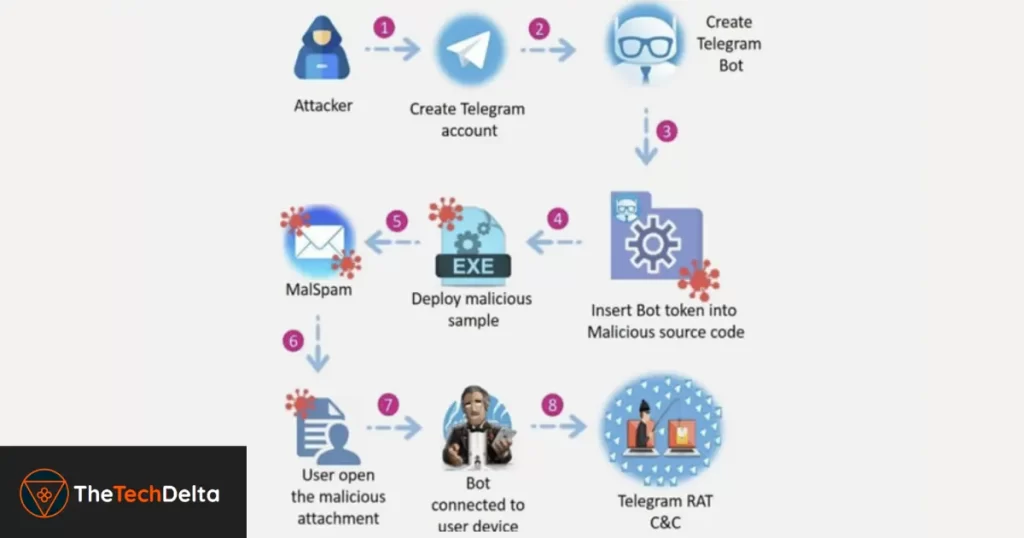
The anatomy of ToxicEye’s attack chain is intricate yet strategic. The attacker initiates the assault by creating a Telegram bot, embedding it into the RAT’s configuration file.
This configuration file is then compiled into an executable, often masked with innocuous names like “paypal checker by saint.exe.” The final stroke involves injecting this executable into a decoy Word document, cleverly named “solution.doc.”
When unsuspecting users open this document, the Telegram RAT (C:\Users\ToxicEye\rat.exe) is downloaded and executed, establishing the connection with the C2 server.
The Growing Trend – Telegram as an Out of the Box C2 System
Check Point’s R&D Group Manager, Idan Sharabi, emphasizes the evolving trend where malware authors are increasingly leveraging Telegram as a ready-made command-and-control system for malware distribution.
This exploitation capitalizes on the widespread use and acceptance of Telegram in various organizations, providing cyber attackers with a means to bypass security restrictions effectively.
Conclusion
In conclusion, the symbiotic relationship between ToxicEye malware and Telegram poses a serious threat to organizations globally. As cybercriminals continue to evolve their tactics, it is imperative for cybersecurity professionals to remain vigilant and proactive.
Organizations must reinforce their security measures, educate users about potential threats, and collaborate across sectors to stay one step ahead of the ever-adapting cyber adversaries. The battle against ToxicEye and similar threats requires a united front, with cybersecurity at the forefront of the defense strategy.
If you found these security learnings valuable, don’t miss out on more exclusive content. Follow us on Twitter and Instagram to stay informed about emerging threats and developments.
Check out the Cyber Safety Section and Subscribe our Newsletter, Join our community and gain access to the latest cybersecurity trends to bolster your defense against evolving threats & associated risks🙂



