In today’s digital world, there are always new dangers waiting to catch us off guard. Recently, a sneaky threat called TunnelVision has emerged 😓
It’s like a hidden path that allows bad actors to sneak a peek at what you’re doing online, even when you believe you’re safe using a VPN.
lets understand TunnelVision in more depth and understand how its impacting the cybersecurity landscape in depth.
Also Read : LockBit Ransomware Mastermind Exposed
Understanding TunnelVision
TunnelVision works like a secret path, sneaking past VPN defenses 😟
It exploits a vulnerability within the Dynamic Host Configuration Protocol (DHCP), a fundamental communication protocol used by devices to obtain network configuration settings.
By leveraging a specific DHCP option known as option 121, attackers can redirect network traffic away from the secure confines of a VPN, leaving it susceptible to interception and manipulation.
How TunnelVision Works
Visualize yourself on a digital highway, shielded by the protective layers of your VPN, confident in your safe navigation.
All seems well until an unexpected obstacle emerges as a deceptive toll booth, manned by a malicious actor disguised as an illicit DHCP server.
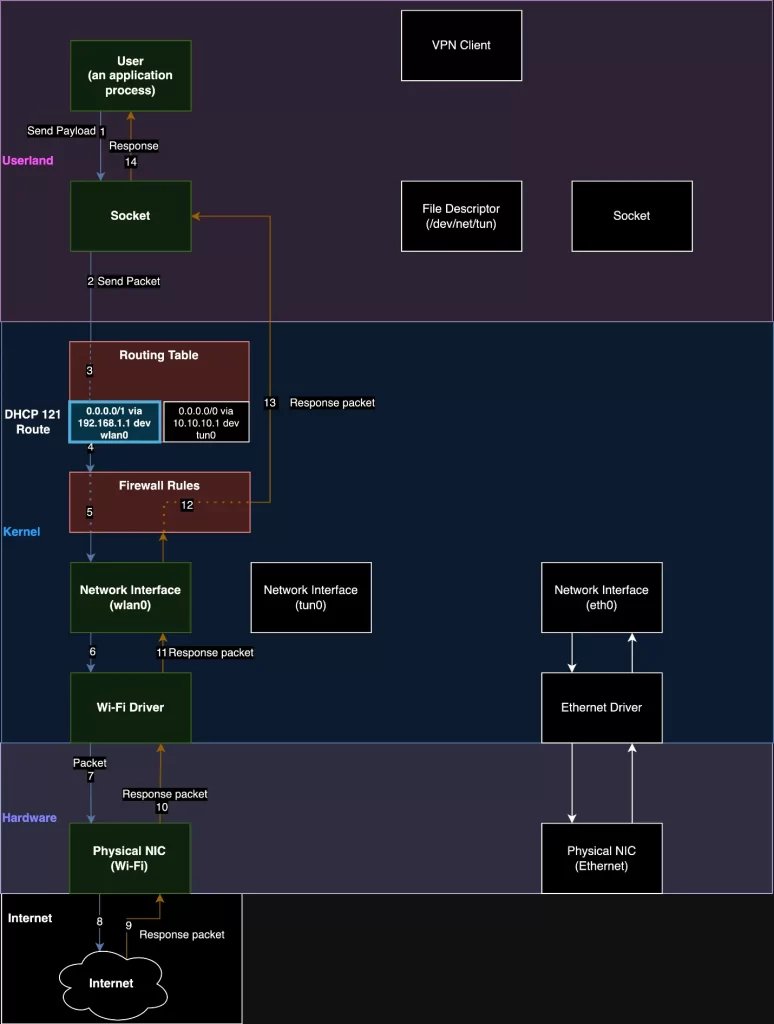
As your device unwittingly passes through this fraudulent checkpoint, it undergoes a stealthy redirection onto an alternate path under the attacker’s control.
In this sudden turn of events, your previously secure data finds itself exposed, susceptible to unauthorized surveillance or manipulation without your awareness or consent.
Implications for Cybersecurity
The alarming aspect of TunnelVision lies in its indiscriminate nature, which means it doesn’t discriminate.
It doesn’t matter which VPN provider you’re using or how you’ve configured it, TunnelVision can still pose a threat to your security.
This wide-ranging impact underscores the urgency of addressing this vulnerability promptly.
It’s crucial to take action to safeguard the confidentiality and security of online communications for users across various platforms and implementations.
Technical Details and Vulnerable Systems
TunnelVision’s exploitation of DHCP weaknesses extends its reach to encompass a wide array of operating systems, including Windows, macOS, and Linux, among others.
It doesn’t discriminate, it affects almost every major operating system out there. Even VPN tools reliant on routing protocols for protection are not immune to its subversive tactics.
This means that not only are individual users at risk, but also organizations relying on VPNs to safeguard their data.
It’s a widespread issue that demands attention. Notably, while Android remains resilient against this particular attack vector, other platforms remain susceptible to its pernicious effects.
This discrepancy underscores the need for comprehensive security measures across all platforms.
It’s a constant game of cat and mouse in the cybersecurity world, where attackers are always looking for new ways to exploit vulnerabilities.
As such, it’s essential for users and organizations alike to stay vigilant and adopt proactive security measures to mitigate the risks posed by TunnelVision and similar threats.
Mitigation Strategies
To counteract the threat posed by TunnelVision, organizations must fortify their network defenses with robust security measures.
Implementing technologies such as DHCP snooping, Address Resolution Protocol (ARP) protections, and stringent port security protocols can bolster resilience against such attacks.
Additionally, leveraging network segmentation techniques, such as network namespaces in Linux environments, can help mitigate the impact of potential breaches.
Conclusion
TunnelVision serves as a stark reminder of the dynamic nature of cybersecurity threats, necessitating continuous vigilance and proactive measures to safeguard against emerging risks.
By fostering awareness and implementing comprehensive security protocols, individuals and organizations can enhance their resilience against the pervasive threat of online intrusions. Stay informed, stay protected, and navigate the digital landscape with confidence.
If you found these security learnings valuable, don’t miss out on more exclusive content. Follow us on Twitter and Instagram to stay informed about emerging threats and developments.
Check out the Cyber Safety Section and Subscribe our Newsletter, Join our community and gain access to the latest cybersecurity trends to bolster your defense against evolving threats & associated risks 🙂



